Power BI Lineage Scanner
Scanned and supported objects
|
The scanner automatically generates lineage metadata for all currently supported sources and connections. However, lineage coverage might vary depending on system capabilities, dynamic transformations, or access permissions. While we strive for comprehensive lineage capture, certain dataflows and transformations might be incomplete or unavailable due to technical constraints. We continuously work to expand coverage and accuracy. |
For a detailed breakdown of supported features and known limitations, see Power BI Scanner Supported Features and Limitations.
Supported connectivity
-
Connector type: REST API.
-
Authentication method: OAuth 2.0 Client Credentials Flow (Service Principal).
Server side configuration
REST API permissions to access Admin - WorkspaceInfo GetScanResult
The user account used for lineage scanning must have administrator rights (such as Microsoft 365 Global Administrator or Power BI Service Administrator), or authenticate using a service principal.
When running under service principal authentication, the service principal app must not have any admin-consent required permissions for Power BI set in the Azure portal.
For more details, see the Microsoft documentation.
Access to Power BI workspaces
The user account needs to have access rights to a given workspace in Power BI.
-
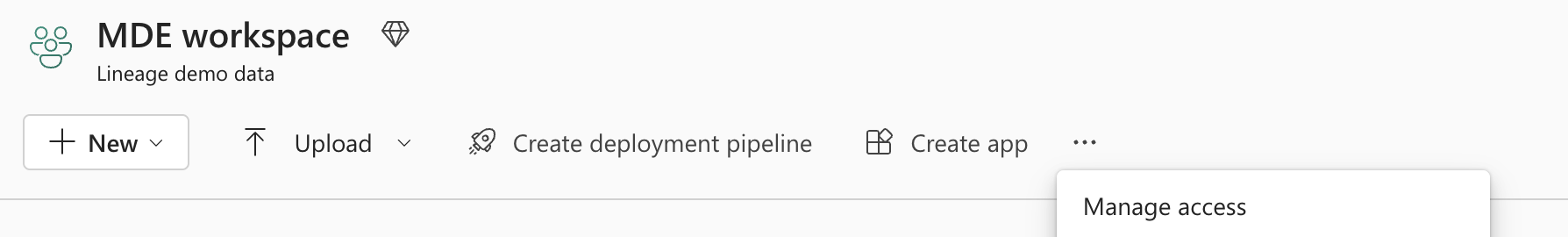
To manage access for the Power BI workspace, locate the workspace you want to scan in Power BI.
-
Select Manage access and setup admin rights for the Azure Power BI scan entity.
Enable tenant settings for metadata scanning
The following tenant settings that control metadata scanning need to be configured. To do this, go to Admin portal > Tenant settings > Admin API settings.
-
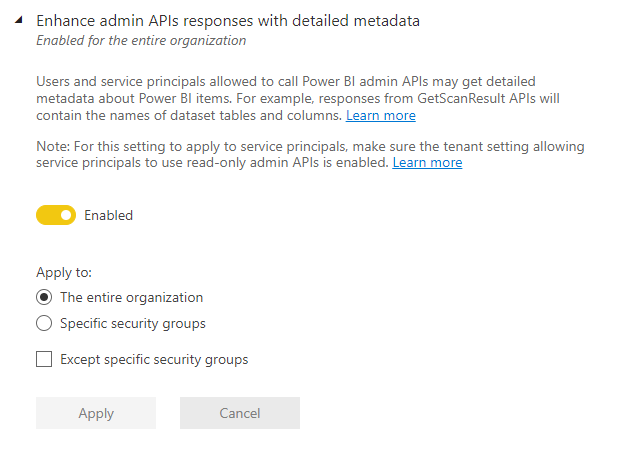
Enhance admin APIs responses with detailed metadata: Turns on model caching and enhances API responses with low-level semantic model metadata (for example, name and description) for tables, columns, and measures.
-
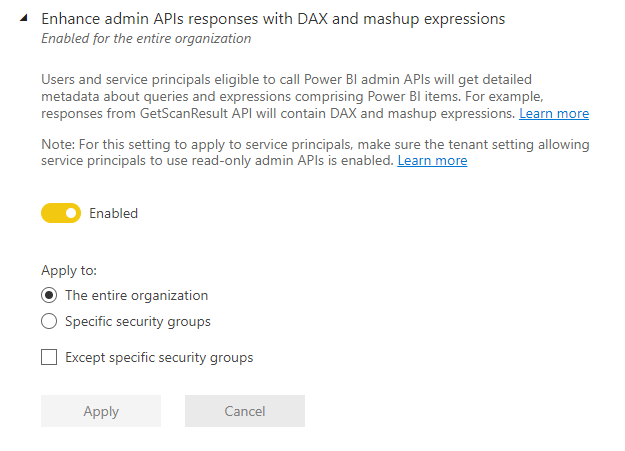
Enhance admin APIs responses with DAX and mashup expressions: Allows the API response to include DAX expressions and Mashup queries. The setting can only be used if the first setting is also configured.
Scanner configuration
All fields marked with an asterisk (*) are mandatory.
| Property | Description |
|---|---|
|
Unique name for the scanner job. |
|
Specifies the source type to be scanned.
Must contain |
|
A human-readable description of the scan. |
|
List of Ataccama ONE connection names for future automatic pairing. |
|
Path to the PowerQueryParser execution file. |
|
URL of the Power BI REST API endpoint. |
|
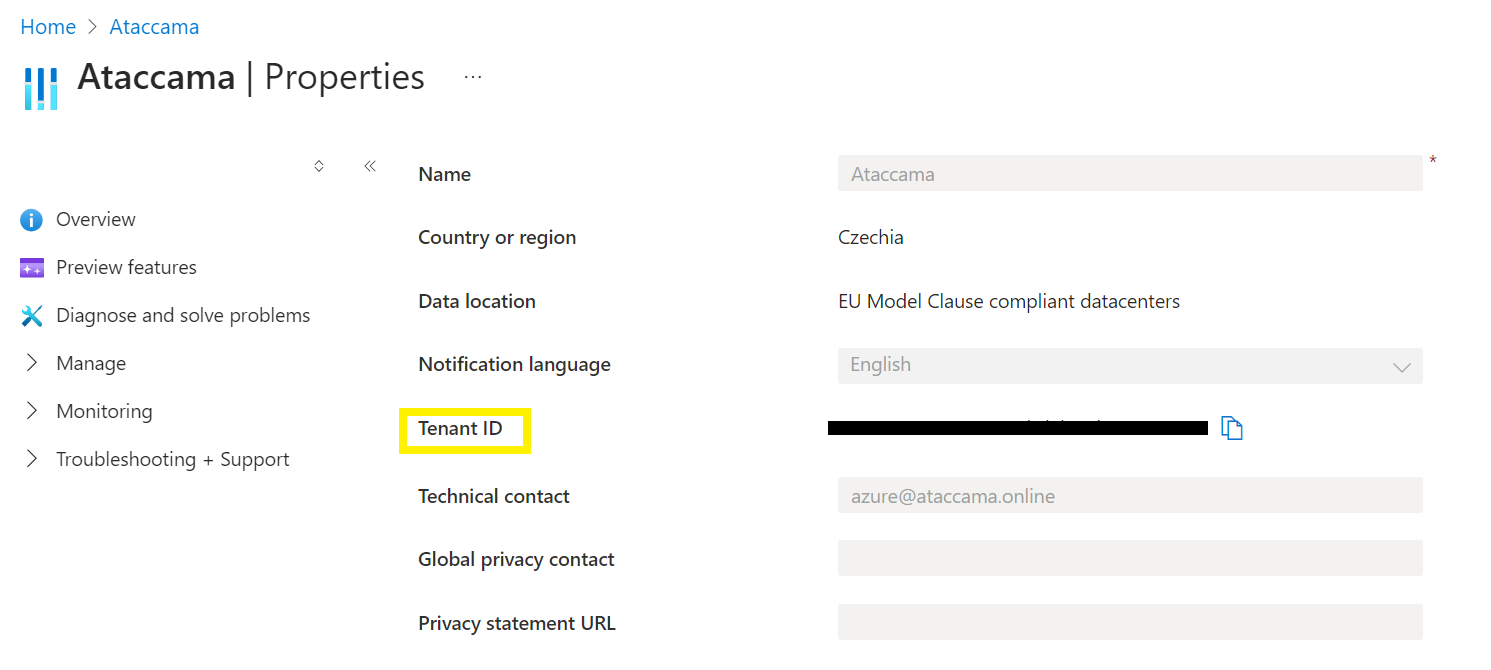
REST endpoint for Microsoft OAauth 2.0. The URL should contain the tenant ID of your organization. |
|
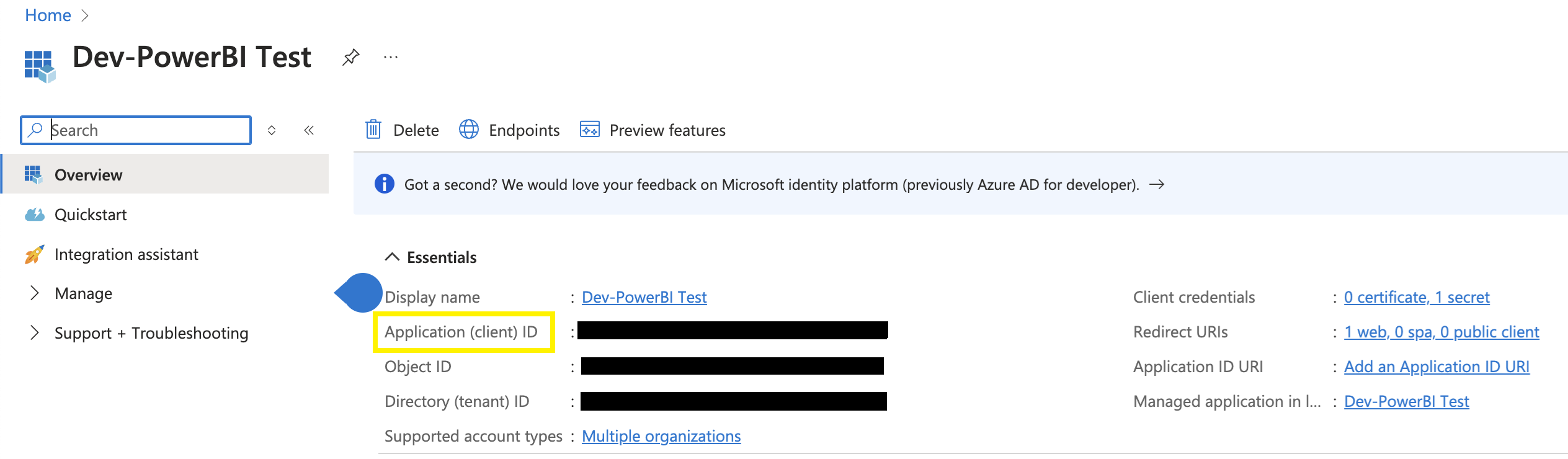
Microsoft 0Auth 2.0 credentials client ID. See Client ID in Azure. |
|
Microsoft OAuth 2.0 credentials client secret. |
|
List of workspace IDs to be excluded from the scan. |
|
List of workspace IDs to be scanned. If left empty, the scanner scans everything. |
{
"scannerConfigs": [
{
"name": "Power BIJob1",
"sourceType": "POWER_BI",
"description": "Scan Power BI platform",
"oneConnections": [],
"inputDataCatalogFilePath": null,
"powerQueryParserPath": "@@ref:env:[POWERQUERY_PARSER]",
"tokenUrl": "https://login.microsoftonline.com/[tenantID]/oauth2/v2.0/token",
"apiUrl": "https://api.powerbi.com/v1.0/myorg",
"clientId": "your-client-id",
"clientSecret": "@@ref:ata:[POWER_BI_CLIENT_SECRET]",
"workspaces": [
"workspace-id1-to-include",
"workspace-id2-to-include"
]
}
]
}Was this page useful?