Overview
With the user management system in ONE Platform, you can configure the authorization privileges of your employees, secure access to your data, and define stewardship for your data assets. This helps you determine user rights and limits while working with data, as well ensure all users have the appropriate rights to particular assets in ONE.
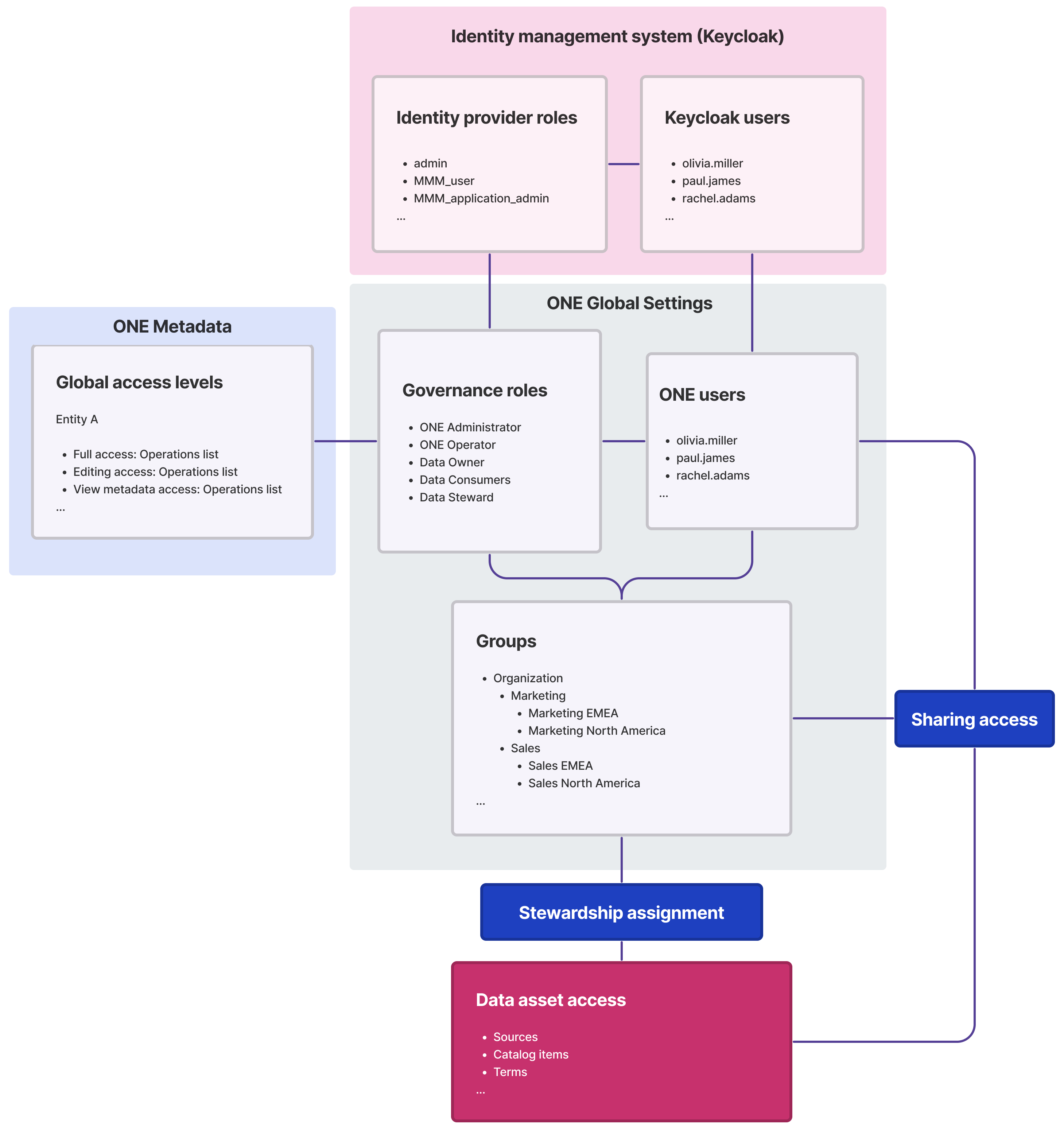
When managing user access in ONE, keep in mind the following principles:
-
You can provide access to particular users. The list of users (people) is loaded from the identity management system you are using, for example, Keycloak, Active Directory, and LDAP authentication. See Users.
-
You can organize users into groups. Groups build a hierarchy that helps illustrate the distributed responsibilities of users working with data assets (
entities) in ONE and sets the sharing access behavior. See Groups.When you start ONE for the first time, only admins have access to data in ONE. Therefore, you must provide (share) access to data with particular groups or specific users. -
You can manage group and user access rights by assigning identity provider roles to users in your identity management system (for example, Keycloak) and creating a team of users connected by similar responsibilities on data. These roles specify the user roles defined in your company. See Identity Provider Roles.
-
Governance roles represent the different action sets available on particular entities for a specific access level. These roles represent various roles of users within a group. Governance roles can be assigned to either a user or an identity provider role. See Governance Roles.
-
You can provide access to particular entities by setting access levels for groups and specific users. Access levels determine the depth of provided access and correspond to the set of operations (basic actions) that the assignee is allowed to perform on each entity. The list of operations depends on the entity type. Custom operation sets can be configured on each entity for every access level. See Access Levels.
-
You can assign stewardship to select the owner group of data assets. This automatically configures the appropriate level of access to the assets the group owns depending on the roles of the group members. This is the recommended approach for managing access to your data assets. See Stewardship.
-
You can provide access to specific entities with the Share feature. See Share Access to Assets.
-
Listing screens also let you manage access to assets and stewardship in bulk. See Share Access and Assign Stewardship in Bulk.
-
You can manage access to protected data for specific groups and users with data protection classification. See Data Protection Classification.
Was this page useful?
