Architecture Overview
Ataccama ONE Platform as a Service (PaaS) is hosted on Amazon Web Service (AWS) or Microsoft Azure cloud depending on your preference.
Within either cloud, you can select a region or geography where the service will be hosted in, with minimal requirements in terms of available services (see Appendix 1). Simply put, the PaaS model means you get to focus on the things that really matter to your organization.
Hardware and software maintenance, operating system patching and upgrades, networking and security are the responsibility of Ataccama while you take care of users and their rights within the system, the data and the surrounding processes depending on how the system fits in your organization.
The following table provides an overview of how responsibilities are shared between you and Ataccama, depending on the selected deployment mode (the asterisk designates Ataccama’s responsibilities).
| On-Premise deployment | PaaS |
|---|---|
User identity and access |
User identity and access |
Data |
Data |
Application usage |
Application usage |
Application maintenance |
Application maintenance* |
Guest OS |
Guest OS* |
Virtualization |
Virtualization* |
Security |
Security* |
Network |
Network* |
Infrastructure |
Infrastructure* |
Physical |
Physical* |
| In hybrid deployment, Data Processing Engine (DPE) is moved to your organization’s system, which means the module falls outside of Ataccama’s scope of responsibility. For more information, see Hybrid Deployment Architecture. |
Ataccama ONE PaaS deployment options
Ataccama ONE PaaS solution can be deployed in one of two distinct ways:
-
Pure PaaS deployment: All components of the Ataccama ONE Platform are run and operated by Ataccama and hosted on AWS or Azure cloud.
-
Hybrid PaaS deployment: All components of the Ataccama ONE Platform with the exception of Data Processing Engine (DPE) are run and operated by Ataccama and hosted on AWS or Azure cloud. In this setup, you run and operate DPE in your corporate network.
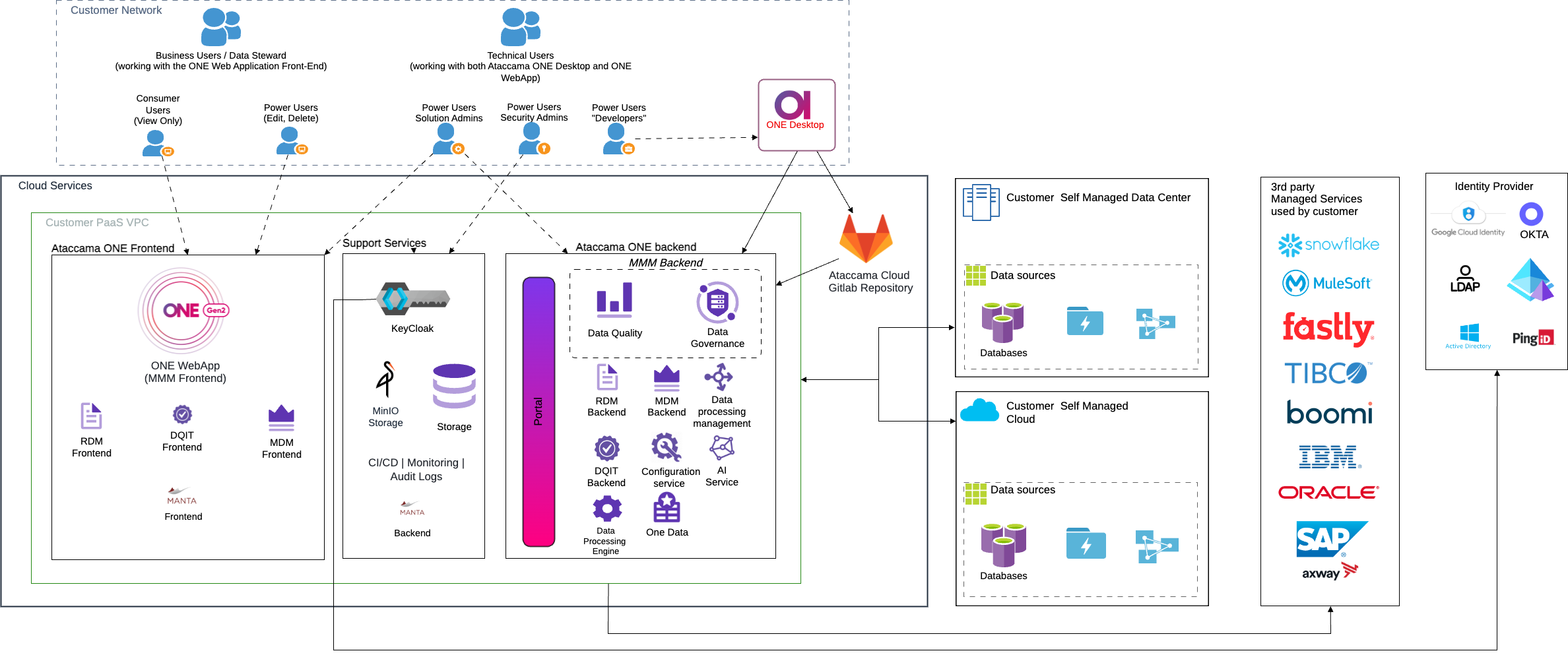
Pure PaaS deployment
The following diagram shows the pure PaaS layout, where all Ataccama components are hosted in the AWS or Azure cloud. In this case, Ataccama is fully responsible for operating, maintaining, and upgrading the Ataccama ONE Platform.
Hybrid PaaS deployment
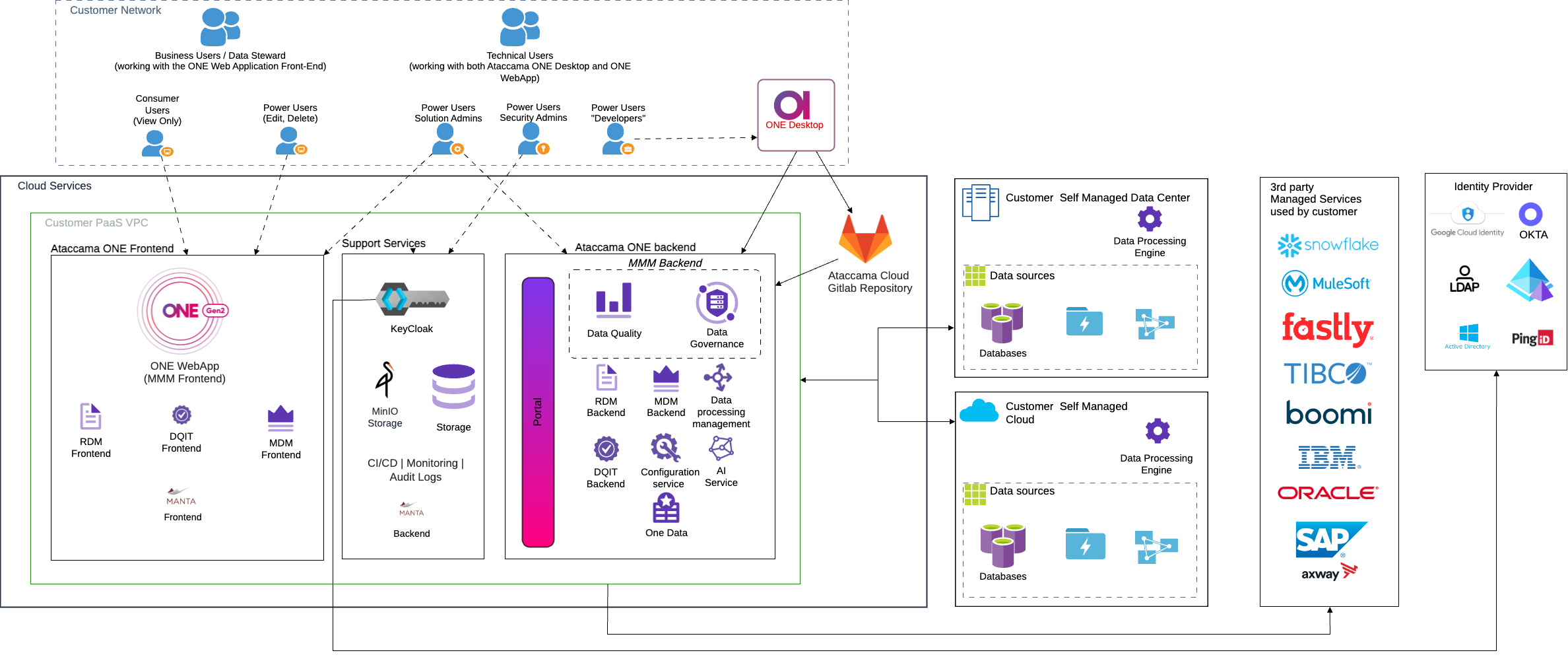
With the hybrid approach, your organization hosts and operates one or more Ataccama components inside your corporate network. Although at first glance this might seem counterintuitive, given that Platform as a Service implies that Ataccama runs and operates the platform on your behalf, this solution is particularly well suited for cases when one of the following conditions must be met:
-
Legal or regulatory requirements: The hybrid approach is typically used in cases when data must be restricted to a certain location or network due to legal or other requirements. As DPE processes your data and produces metadata about your data and data sources, it is the only module that needs to access your data sources.
If your instance of ONE includes the Ataccama ONE MDM Suite, MDM and RDM contain your master and reference data respectively and might therefore be subject to the same requirements as your other data sources.
In this case, or in case your metadata also needs to remain within your corporate network, Ataccama offers a fully self-hosted installation where you host, operate, and run the Ataccama software on (virtual) machines in your data center or with any cloud provider of your choice.
This way, you can fully respect your company policies about data mobility while making full use of all Ataccama tools.
-
Network limitations: To produce metadata about your data sources, DPE must first read the database contents. Depending on how large the data source is and whether there are any network limitations such as insufficient bandwidth or latency, this process could become inefficient and time-consuming or run into issues.
These issues are easily resolved if DPE is hosted inside your network close to your data sources. In this case, instead of all information available, only a fraction of the metadata is transmitted to Ataccama ONE PaaS. In addition, DPE can be configured to use bidirectional communication with the Ataccama cloud or to poll the Ataccama cloud periodically, which ensures that all communication with Ataccama ONE PaaS can only be initiated from your side.
If you are working with a variety of data sources, with some residing in a highly restricted environment, you can also opt for a solution in which some DPE instances are set up within the restricted network while your remaining data sources are processed by DPEs installed outside that network or even within the Ataccama cloud.
The following diagram shows the hybrid PaaS layout where DPEs are located in your network. For more detailed information about the hybrid PaaS, including architecture, network settings and communication details, data flows, DPE sizing and installation instructions, see Hybrid Deployment Architecture and Hybrid Deployment.
Backups and data recovery
The Ataccama ONE PaaS solution ensures protection against disasters and service disruption thanks to the high availability (HA) design of its components and the backup and restore services that it provides. Backup and restore services cover both the customer data and the PaaS configuration and settings. For more detailed information, Backup and Restore Architecture.
Appendix 1: Ataccama ONE PaaS deployment locations
Ataccama PaaS can be deployed in a geography, region, and availability zone of your choice provided that the following services are available in those locations and that the location has sufficient hardware capacity.
- AWS
-
-
Multiple availability zones (AZ)
-
EKS support
-
PostgreSQL RDS
-
m5a.2xlarge nodes
-
- Azure
-
-
Multiple availability zones (AZ)
-
AKS support
-
Azure PostgreSQL Server
-
Dsv3-series nodes available
-
| Although this is a rare occurrence, cloud providers occasionally might not have sufficient capacity to allow for new deployments at that time. If this happens, Ataccama can assist you in identifying alternative deployment locations and working with the cloud provider to determine a date when the selected location would again be available, therefore helping you make an informed decision on how to proceed. |
Was this page useful?
