MDM Web App Security Configuration
Authentication
Configure client URLs in Keycloak
Edit the following clients in Keycloak following the steps described in this section:
-
mdm-admin-client -
mdm-token-client-
Open the Keycloak administration console.
-
Make sure Ataccamaone realm is selected.
-
Select Clients.
-
From the list of clients, select the client identifier to open the configuration.
-
Depending on the client Access Type setting, different configuration fields are available and filled in.
Edit all filled-in fields that contain URLs, for example, Valid Redirect URIs, Base URL, and Admin URL.
Change the
http://localhost:<port>part to the actual client location. -
Select Save.
-
Repeat steps 3-7 for all relevant clients.
To change the default client password, switch to the Credentials tab of the client configuration and click Regenerate Secret. For basic authentication, enable Direct Access Grants Enabled option in the Keycloak client. 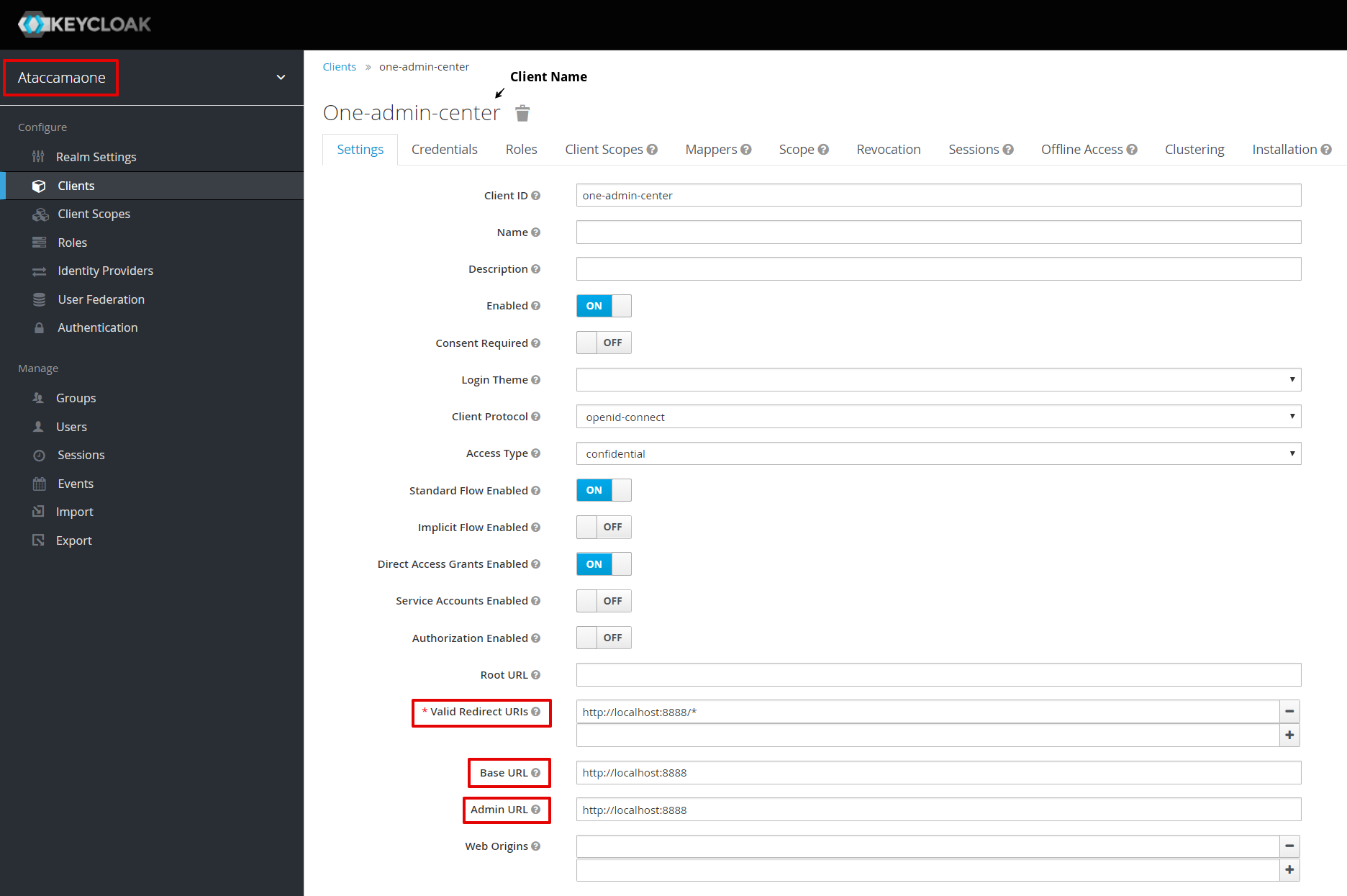
-
Edit client configuration files
To define the configuration for your Keycloak clients, add or edit the Keycloak configuration section in the MDM Server application.properties file.
The settings should correspond to the Keycloak settings for the clients.
| Keycloak is case-sensitive. Make sure to use lowercase if referring to the Keycloak server URL via hostname. |
The following is a sample configuration for MDM Web App:
| Name | Default value | Mandatory | Description |
|---|---|---|---|
|
ataccamaone |
Yes |
Keycloak realm. |
|
http://localhost:8083 |
Yes |
Keycloak base URL. |
|
$\{ataccama.authentication.keycloak.base-url}/auth |
Yes |
Keycloak server URL. Ending with |
|
mdm-admin-client |
Yes |
Admin Keycloak client ID. |
|
mdm-admin-client-s3cret |
Yes |
Admin Keycloak client secret. |
|
mdm-token-client |
Yes |
Token Keycloak client ID. |
|
mdm-token-client-s3cret |
Yes |
Token Keycloak client secret. |
|
$\{ataccama.authentication.keycloak.server-url}/realms/$\{ataccama.authentication.keycloak.realm} |
Yes |
Token Keycloak issuer. |
| For information about how to encrypt passwords, see Encrypt Passwords. |
Edit the following client adapter files so that MDM Web App connects to Keycloak properly:
-
On the web application server, edit
mdm/etc/application.properties.ataccama.authentication.keycloak.realm=ataccamaone ataccama.authentication.keycloak.server-url=http://localhost:8083/auth ataccama.authentication.keycloak.token.client-id=mdm-webapp-public-client # Keycloak public client ID for web application browsing ataccama.authentication.keycloak.public.client-id=$\{ataccama.authentication.keycloak.token.client-id} ataccama.authentication.keycloak.token.secret=mdm-webapp-public-client-s3cret ataccama.authentication.keycloak.token.issuer=$\{ataccama.authentication.keycloak.server-url}/realms/$\{ataccama.authentication.keycloak.realm}For information about how to encrypt passwords, see Encrypt Passwords. -
In the project configuration
Files/etc/issue_management/directory, edit the DQITconfig.xmlfile.
In most cases, it is only necessary to modify the ataccama.authentication.keycloak.server-url attribute, which corresponds to the base URL of the Keycloak server.
Treat other settings as expert and modify only if you know what you are doing.
| Keycloak is case-sensitive. Make sure to use lowercase if referring to the Keycloak server URL via hostname. |
Web application security
You can configure MDM Web App security by adding response headers (security headers) to HTTP responses from the web application.
| We recommend setting security headers in case your web application is exposed to potential security attacks. |
The security headers are configured in MDM Web App application.properties file.
They are commented out by default: uncomment them to enable.
| Name | Default value |
|---|---|
|
'self' ${ataccama.authentication.keycloak.server-url} |
|
* 'unsafe-inline' 'unsafe-eval' |
|
'self' data: |
|
deny |
|
none |
|
strict-origin |
|
1; mode=block |
|
nosniff |
Was this page useful?
