Add Driver Properties
When creating a new connection or editing an existing one, you can make it driver-dependent and enable additional authentication methods. This article contains driver properties you need to set for such use cases.
| Not all deployment types support all authentication methods. |
How to add driver properties?
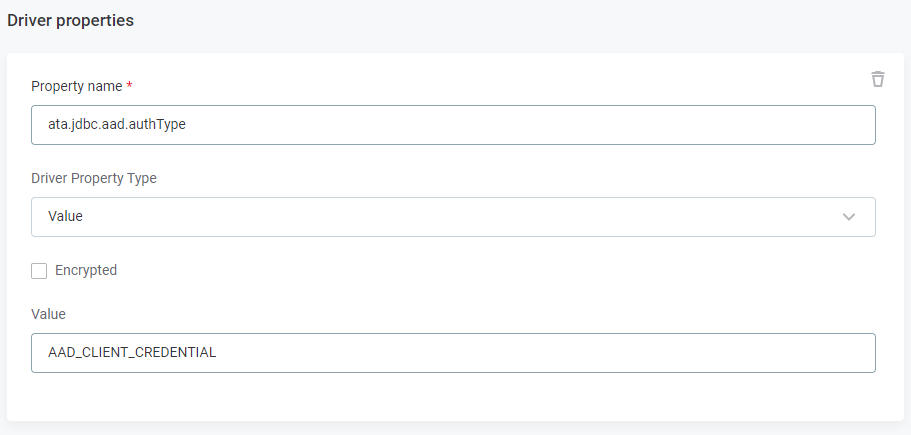
When creating or editing a source connection (Sources > [your source] > Connections), select Add Driver Property in Driver Properties.
For each property, you need to provide a name and choose whether the property takes a value or file (Driver Property Type).
Select Encrypted to encrypt the property value or file content. This is recommended for client secrets and passwords.
Finally, enter a value or upload a file depending on the property type selected.
Mutual SSL authentication
Oracle
To enable mTLS for your Oracle data source, add the following driver properties:
| Property | Type | Encrypted | Description |
|---|---|---|---|
|
File |
Yes |
The filename of your keystore. |
|
Value |
Yes |
The password to your keystore. |
|
File |
No |
The filename of your domain trust store. |
|
Value |
Yes |
The password to your domain trust store. |
|
Value |
No |
(TCPS) |
|
Value |
No |
1.0 |
Then use the following credentials to connect:
| Username | Password |
|---|---|
|
|
PostgreSQL
To enable mTLS for your PostgreSQL data source, add the following driver properties:
| Property | Type | Encrypted | Description |
|---|---|---|---|
|
Value |
No |
|
|
File |
No |
The filename of your client SSL certificate. |
|
File |
No |
The filename of your root SSL certificate. |
|
File |
Yes |
The name of the file that contains your private SSL key. |
Then use the following credentials to connect:
| Username | Password |
|---|---|
|
|
Azure Active Directory authentication
Azure Key Vault authentication
| We highly recommend configuring Key Vault authentication using the Secret Management Service rather than driver properties. Once you have configured Key Vault in the Secret Management Service you can retrieve credentials when creating new datasource connections. |
To access Azure Key Vault using Azure Active Directory (AD) Managed Identity, add the following driver properties:
ata.jdbc.keyvault.authType = AAD_MANAGED_IDENTITY
ata.jdbc.aad.keyvault.vaultUrl = <key vault URL (https://your-vault-name.vault.azure.net)>To access Azure Key Vault using Azure AD Client Credential, add the following driver properties:
ata.jdbc.keyvault.authType = AAD_CLIENT_CREDENTIAL
ata.jdbc.aad.keyvault.tenantId = <tenant ID of your subscription (UUID format)>
ata.jdbc.aad.keyvault.clientId = <service principal client ID (UUID format)>
ata.jdbc.aad.keyvault.vaultUrl = <key vault URL (https://your-vault-name.vault.azure.net)>
ata.jdbc.aad.keyvault.clientSecret = <service principal client secret>Snowflake with Azure Service Principal
To use Snowflake with Azure AD Service Principal, add the following driver properties:
authenticator = OAUTH
ata.jdbc.aad.authType = AAD_CLIENT_CREDENTIAL
ata.jdbc.aad.tenantId = <tenant ID of your subscription (UUID format)>
ata.jdbc.aad.clientId = <service principal client ID (UUID format)>
ata.jdbc.aad.clientSecret = <service principal client secret>
ata.jdbc.aad.resource = https://<UUID>Snowflake with Azure Service Principal and Azure Key Vault
To use Snowflake with Azure AD Service Principal with the secret stored in Azure Key Vault, add the following driver properties:
authenticator = OAUTH
ata.jdbc.aad.keyvault.authType = AAD_CLIENT_CREDENTIAL
ata.jdbc.aad.keyvault.tenantId = <tenant ID of your subscription (UUID format)>
ata.jdbc.aad.keyvault.clientId = <service principal client ID (UUID format)>
ata.jdbc.aad.keyvault.clientSecret = <client secret for key vault> <!--Recommended to store as encrypted. -->
ata.jdbc.aad.keyvault.vaultUrl = <key vault URL (https://your-vault-name.vault.azure.net)>Once these authentication properties are set, you can insert secrets from the Key Vault into other driver properties:
authenticator = OAUTH
token = SECRET:snowflake-ad
ata.jdbc.aad.keyvault.authType = AAD_CLIENT_CREDENTIAL
ata.jdbc.aad.keyvault.tenantId = 5310c2d9-21a8-4ace-c4ab-ac46ac770517
ata.jdbc.aad.keyvault.clientId = 5f74a1f7-024c-12df-fa42-fd7dc3efd81a
ata.jdbc.aad.keyvault.vaultUrl = https://mycompany-vault.vault.azure.net
ata.jdbc.aad.authType = AAD_CLIENT_CREDENTIAL
ata.jdbc.aad.tenantId = 8340c229-a1c8-42c9-fd2b-abf6ac170d85
ata.jdbc.aad.clientId = dbda8a9f-976c-42a1-badb-d8efd826ceaf
ata.jdbc.aad.clientSecret = keyvault:SECRET:snowflake-ad
ata.jdbc.aad.resource = https://51a1c2d7-5479-4107-c1fc-b4a3e14cfef9Databricks with Azure Service Principal
To use Databricks with Azure AD Service Principal, add the following driver properties:
ata.jdbc.aad.authType = AAD_CLIENT_CREDENTIAL
ata.jdbc.aad.tenantId = <tenant ID of your subscription (UUID format)>
ata.jdbc.aad.clientId = <service principal client ID (UUID format)>
ata.jdbc.aad.clientSecret = <service principal client secret>
ata.jdbc.aad.resource = 2ff814a6-3304-4ab8-85cb-cd0e6f879c1d
ata.jdbc.tokenPropertyKey = Auth_AccessTokenDatabricks with Azure Service Principal and Azure Key Vault
To use Databricks with Azure AD Service Principal with the secret stored in Azure Key Vault, add the following driver properties:
authenticator = OAUTH
ata.jdbc.aad.keyvault.authType = AAD_CLIENT_CREDENTIAL
ata.jdbc.aad.keyvault.tenantId = <tenant ID of your subscription (UUID format)>
ata.jdbc.aad.keyvault.clientId = <service principal client ID (UUID format)>
ata.jdbc.aad.keyvault.clientSecret = <client secret for key vault> <!--Recommended to store as encrypted. -->
ata.jdbc.aad.keyvault.vaultUrl = <key vault URL (https://your-vault-name.vault.azure.net)>Once these authentication properties are set, you can insert secrets from the Key Vault into other driver properties.
Databricks with Azure Managed Identities
| The Databricks cluster must be running on the same Azure virtual machine (VM) within the same tenant and the managed identity must be set up for the VM in Azure AD. |
To use Databricks with Azure AD Managed Identities, add the following driver properties:
Databricks Azure AD MSI
ata.jdbc.authType = AAD_MANAGED_IDENTITY
ata.jdbc.aad.resource = 2ff814a6-3304-4ab8-85cb-cd0e6f879c1d
ata.jdbc.tokenPropertyKey = Auth_AccessTokenDatabricks with Azure Managed Identities and Key Vault
| The Databricks cluster must be running on the same Azure virtual machine (VM) within the same tenant and the managed identity must be set up for the VM in Azure AD. |
To use Databricks with Azure AD Managed Identities with Key Vault, add the following driver properties:
ata.jdbc.aad.keyvault.authType = AAD_MANAGED_IDENTITY
ata.jdbc.aad.keyvault.tenantId = <tenant ID of your subscription (UUID format)>
ata.jdbc.aad.keyvault.vaultUrl = <key vault URL (https://your-vault-name.vault.azure.net)>Azure Data Explorer (ADX) with Azure Service Principal
| Applies to 14.5.1 and later. |
To use ADX with Azure Service Principal, add the following driver properties:
ata.jdbc.aad.authType = AAD_CLIENT_CREDENTIAL
ata.jdbc.aad.tenantId = <tenant ID of your subscription (UUID format)>
ata.jdbc.aad.clientId = <service principal client ID (UUID format)>
ata.jdbc.aad.clientSecret = <service principal client secret>
ata.jdbc.aad.resource = https://<adx hostname>
ata.jdbc.tokenPropertyKey = accessTokenAzure Active Directory Kerberos and MS SQL
If you are connecting to an MS SQL data source using Azure Active Directory Kerberos authentication, you need to set additional properties for the JDBC connection string:
integratedsecurity=true
authenticationScheme=JavaKerberosjdbc:sqlserver://mssql.db.hostname:1433;databaseName=test;integratedsecurity=true;authenticationScheme=JavaKerberos;Azure Synapse and Azure Active Directory
Connect to your Azure SQL Database or Azure Synapse Analytics using the MS SQL Server driver.
Azure Synapse with Azure Service Principal
There are two ways to connect to Microsoft Azure Synapse using Azure Service Principal without Azure Key Vault:
-
Add the properties to the JDBC connection string, for example:
jdbc:sqlserver://name.database.windows.net:1433;database=my_database;encrypt=true;trustServerCertificate=false;hostNameInCertificate=*.database.windows.net;loginTimeout=30;authentication: ActiveDirectoryServicePrincipal;AADSecurePrincipalId=<PrincipalID>;AADSecurePrincipalSecret=<PrincipalSecret> -
Add custom driver properties:
Azure Synapse with Azure Service Principalauthentication = ActiveDirectoryServicePrincipal AADSecurePrincipalId = <user-supplied Service Principal ID> ### Recommended to store as encrypted or inject a value from Key Vault "keyvault:SECRET:<secret_name>" AADSecurePrincipalSecret = <user-supplied Service Principal secret>
Azure Synapse with Azure Service Principal and Azure Key Vault
To use Azure Synapse with Azure AD Service Principal with the secret stored in Azure Key Vault, add the following driver properties:
ata.jdbc.aad.keyvault.authType = AAD_CLIENT_CREDENTIAL
ata.jdbc.aad.keyvault.tenantId = <tenant ID of your subscription (UUID format)>
ata.jdbc.aad.keyvault.clientId = <Key Vault client ID (UUID format)>
### Recommended to store as encrypted
ata.jdbc.aad.keyvault.clientSecret = <Key Vault client secret>
ata.jdbc.aad.keyvault.vaultUrl = <key vault URL (https://your-vault-name.vault.azure.net)>Azure Synapse with Azure Managed Identities and Azure Key Vault
To use Azure Synapse with Azure AD Managed Identities with Azure Key Vault, add the following driver properties:
ata.jdbc.aad.keyvault.authType = AAD_MANAGED_IDENTITY
ata.jdbc.aad.keyvault.tenantId = <tenant ID of your subscription (UUID format)>
ata.jdbc.aad.keyvault.clientId = <Key Vault client ID (UUID format)> <!--Optional, not required when used System Assigned Identity -->
ata.jdbc.aad.keyvault.vaultUrl = <key vault URL (https://your-vault-name.vault.azure.net)>Key Vault Secret Injection
Once the Azure Key Vault service is set up using driver properties for the selected data source, secrets from the Key Vault can be injected into any other driver properties.
To insert a client secret from the Key Vault, enter the value keyvault:SECRET:<name_of_secret>.
In the following example, you have two secrets set in your Azure Key Vault called PrincipalID and Secret with two values stored.
Inject values from both of them using the following two properties:
AADSecurePrincipalId = keyvault:SECRET:PrincipalID
AADSecurePrincipalSecret = keyvault:SECRET:SecretWas this page useful?
