Service Overview
Ataccama ONE Platform as a Service brings a standardized, fully automated, and secure environment for your Ataccama ONE data management and data governance solution using one of selected industry-standard cloud providers, Amazon Web Services (AWS) or Microsoft Azure.
Each solution is based on a single-tenant model, where every client has their own instance in a data center location of their choice. This also includes dedicated computing power, a separated network and access points, along with monitoring and management that are centrally handled by Ataccama.
Such a setup ensures quick ramp-up possibilities and easy user onboarding while in turn eliminating the need to consider hardware and software requirements or product installations.
Depending on your Ataccama ONE product suite, your current environment, and your needs, Ataccama ONE PaaS can be delivered in a number of standardized yet flexible deployment options. In addition, the solution supports several types of integrations with customer-managed data sources or third-party data services.
Architecture overview
The Ataccama ONE PaaS architecture is based on modern cloud principles with a container-based environment, cloud native tools, and a high level of automation. It is designed as a single-tenant solution, hosted in a dedicated customer account (AWS) or subscription (Azure), providing you with your own PaaS instance in a cloud provider’s region of your choice. This does not mean dedicated physical hardware as Ataccama uses the cloud provider’s standard shared hardware and therefore ensures the level of separation between different accounts equal to the one that the cloud providers offer their customers.
| For more information about how AWS and Azure handle account separation and security, see Shared responsibility model and Shared responsibility in the cloud respectively. |
Your data sources, including third-party data management services such as Snowflake, Collibra, and many others, can reside in various environments depending on your setup. Ataccama ONE PaaS offers several secure connection options for integrating with your data sources.
Identity and access management for Ataccama ONE PaaS environments relies on the role-based access control (RBAC) principle. In addition, user management can be integrated with any identity management system supporting the SAML, OAuth 2.0, or OIDC protocol, as well as the Kerberos bridge.
Ataccama continuously monitors the PaaS service functionality and collects all component logs in a centralized, Ataccama-managed monitoring and logging system. The Ataccama Operations team uses the central monitoring for incident management and problem solving.
To ensure the resiliency of your data and configurations, regular data backups are implemented along with a number of disaster recovery scenarios. The following diagram shows the logical architecture of Ataccama ONE PaaS.
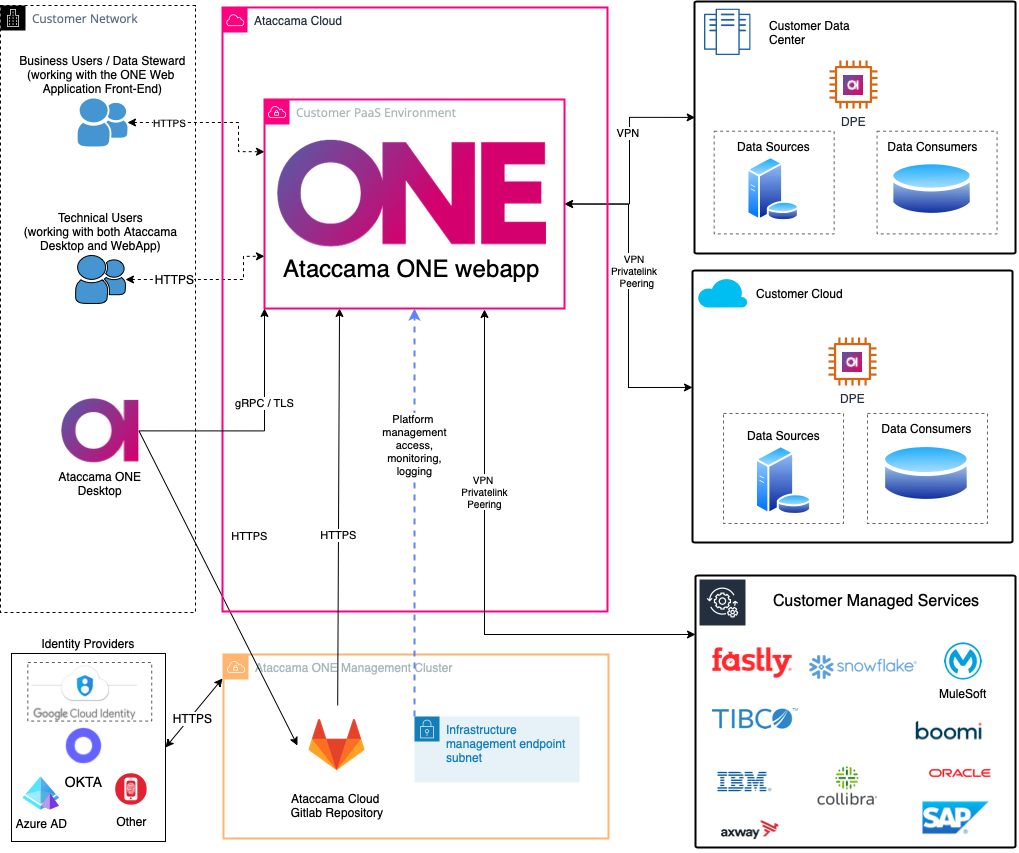
Deployment Variants
Ataccama ONE PaaS offers three deployment options:
-
Standard platform as a service deployment: All components of Ataccama ONE are hosted in the cloud. Connections to self-hosted or third-party data sources are made from the cloud to the data sources. This is the most common deployment variant.
-
Hybrid platform as a service deployment: All components of Ataccama ONE are hosted in the cloud with the exception of Data Processing Engine (DPE).
-
Combination of standard and hybrid deployment: All components of Ataccama ONE are hosted in the cloud, with DPEs located both within Ataccama ONE PaaS and outside of it.
Standard platform as a service
In this deployment mode, the entire platform is hosted in a cloud and cloud location of your choice. When setting up the infrastructure, you only need to allow the Ataccama Platform to connect to your data sources in the cloud, on premise, or hosted on a third-party service. There is no hardware or software to install, maintain, or support.
The key advantage of this offering is that it saves you the hassle of having to support, maintain, or operate any component. On the other hand, as DPE instances need to connect from Ataccama ONE to your data sources and read their contents, this means that it is not suited for organizations whose legal or policy requirements specify that data must not leave the company’s network.
| MANTA is only supported in Ataccama ONE standard platform as a service deployment, where DPEs are also located in the cloud and both MANTA and DPEs have direct network access to data sources. In addition, data lineage is only available for the following databases: PostgreSQL, MS SQL, Oracle, Teradata. |
Hybrid platform as a service
In hybrid deployment mode, all Ataccama components except DPE instances are hosted in a cloud and cloud location of your choice. With this infrastructure, you are responsible for hosting one or more DPEs, which includes maintaining and supporting the hardware on which this software runs. All connections to your data sources, whether on premise, in the cloud, or hosted by a third-party, are made only from the DPE instances that you are hosting.
The main benefit of this setup is that your data remains within your network at all times, which can help you comply with your organization’s requirements.
Supported environments
Ataccama ONE PaaS can be hosted on both Amazon Web Services (AWS) and Microsoft Azure cloud platforms. Regardless of the cloud provider you choose, you get the same functionality, security, and support levels.
On either cloud, your environment is separated from all other customer environments as it runs in a dedicated account (AWS) in the Ataccama AWS Organization or subscription (Azure) in the Ataccama AD Tenant. These accounts or subscriptions are always owned and managed by Ataccama.
All the infrastructure necessary for operating Ataccama ONE PaaS is located within your dedicated environment. A separate environment holds the central monitoring and logging management and the backup infrastructure, which Ataccama support personnel uses to monitor and maintain all customer PaaS environments.
The following table provides information about specific system modules and functions that each type of environment contains.
| Customer dedicated environment | Ataccama ONE PaaS management (shared environment) |
|---|---|
|
|
Ataccama ONE suites
Ataccama ONE PaaS currently supports all Ataccama components and modules released in version 13. This includes:
-
Ataccama ONE Data Governance Suite
-
Ataccama ONE Data Quality and Governance Suite
-
Ataccama ONE MDM Suite (MDM and RDM variants)
The following components and modules are not supported in the PaaS offering as they were released prior to version 13:
-
Big Data Engine (BDE): Now available as ONE Spark DPE, an optional module for Ataccama ONE Data Governance Suite and Ataccama ONE Data Quality and Governance Suite. You can integrate with your Spark cluster through a DPE connector.
-
DQ Dashboard (DQD): Integrated in ONE as part of monitoring projects.
Integrations
Depending on your needs, Ataccama offers multiple options to integrate Ataccama ONE PaaS with your environment, as described in the following sections. Regardless of the option selected, the communication to and from Ataccama ONE PaaS is fully encrypted.
Private Link connection
If you already have a cloud presence, you can connect to Ataccama ONE PaaS using the native AWS or Azure Private Link options. All data source interactions are transferred over the Private Link service.
Peering connection
Ataccama ONE PaaS is able to integrate with Amazon Virtual Private Cloud (VPC) and Azure Virtual Network (VNet) peering connections. All data source interactions are transferred over the peering connection.
VPN connection
Ataccama ONE PaaS also offers a site-to-site VPN. Compared to a remote access VPN, which allows one system to access the corporate network, a site-to-site VPN effectively establishes connection between only one part of the corporate network and another, target network.
This way, from the perspective of business users working with Ataccama ONE PaaS, it looks like the services hosted as part of Ataccama ONE PaaS are available within their corporate network.
Service availability, continuity, and resiliency
Ataccama ONE PaaS is available round-the-clock with a guaranteed uptime of 99% (platform SLA) outside of scheduled maintenance windows. Any scheduled maintenance is announced within the appropriate notice period (typically two weeks in advance) and is therefore not counted as unavailability of the solution.
To prevent data corruption or loss, a backup service is available as an integral part of the Ataccama ONE PaaS service. The backup service covers both your data and configurations as well as platform settings and configuration. There are also restore and disaster recovery scenarios in place covering up to the whole region loss. For more details, see Backup and Restore Architecture.
Recovery Point Objectives (RPOs) and Recovery Time Objectives (RTOs) values are defined as follows:
-
RPO: 1 hour
-
RTO: 48 hours
The Ataccama ONE PaaS offering uses cloud provider’s native services to store your data, which by design ensures high availability in the designated region. All these services also include automatic failover, resiliency against the loss of the primary availability zone, and 99,999999999% durability ("eleven nines").
Responsibility matrix
The Ataccama PaaS is used for hosting Ataccama ONE on AWS or Microsoft Azure. As a result and as part of the shared responsibility model, distinct security responsibilities exist between you, Ataccama, and the chosen cloud provider:
-
As part of the service, Ataccama takes care of the application security, operating system, data, and network configuration.
-
AWS or Microsoft Azure are responsible for the physical security of the data centers and the infrastructure.
-
You are responsible for the security of your own data sources and the identity and access management settings for your employees.
PaaS operations
Ataccama ONE PaaS also includes managed services covering the platform and integrations. Maintaining, updating, and problem solving of Ataccama ONE PaaS environments are the responsibility of the Ataccama Operations team, which offers support 24/7.
To get in touch, use the Ataccama Service Desk or other communication paths as specified in your contract.
Incident management
To ensure the level of functionality agreed in the SLAs, incident management in Ataccama implements a number of well-defined processes for handling events that can potentially impact the availability or integrity of your Ataccama ONE PaaS environments. These procedures involve identifying, escalating, mitigating, and reporting incidents. Based on how urgent the situation is, all issues are first categorized by priority, with the highest priority reserved for issues affecting your ability to use the service.
The following table shows how issues are classified:
| Severity | Description |
|---|---|
P0 | Blocker |
The production system is down, which includes one of the following:
|
P1 | Critical |
A critical business process of the platform is impaired, causing a serious disruption of a major, daily business function. There is no acceptable workaround. |
P2 | Major |
A non-critical issue has occurred that affects the software or a non-production environment. The customer is able to use the platform and there is an acceptable workaround for the issue. |
P3 | Minor |
An inquiry or low impact issue that does not require immediate attention, such as cosmetic issues on screens, issues in documentation, or a request regarding the use of the platform. |
Change management
Similarly to incident management, change management is another well-defined process that ensures reliable and seamless implementation of changes and updates on Ataccama ONE PaaS. The PaaS product is built using infrastructure as code (IaC) approach based on HashiCorp Terraform that uses a declarative coding format. As a result of this configuration, any changes to the infrastructure are handled through Terraform.
All Terraform code is held within a central repository on GitLab that tracks all changes in the code and requires approval from a second cloud engineer before taking effect. Thanks to this, the four-eye principle is maintained.
Change requests can be initiated from various sources, for example, it could be a customer requirement, regular update, security patch, or output from the incident solving process. Requests are submitted and registered through one of the two channels:
-
A JIRA ticket containing the change request submitted to the cloud team.
-
Internal Slack communication describing the change that is then submitted using GitLab or JIRA.
Each change request is evaluated from a business, operation, and security compliance point of view. Based on the output of the evaluation, a designated architect or cloud engineer makes a go/no go decision. The change is then assigned to one or more engineers who plan, review, and implement the change. Changes affecting customer-facing services are completed during the agreed upon maintenance window.
Security and data privacy
Security and data privacy features and processes are an integral part of Ataccama ONE PaaS. Their purpose is to ensure availability and operability of the platform while keeping an appropriate level of data and operational security. The Ataccama ONE PaaS security and privacy architecture consists of several well-established and integrated components:
-
Security processes and best practices
-
Infrastructure security
-
User access management
-
Application security
-
Integrations security
-
Customer data security and privacy
For more details, see security-overview.adoc.
Was this page useful?
