Admin Access to Keycloak via SSO
By default, platform administrators use a single shared account with fixed credentials to access the Keycloak Admin Console. This presents security and governance challenges, as multiple administrators share the same credentials without individual accountability.
Configuring SSO access to Keycloak enables administrators to:
-
Log in with their individual accounts instead of shared credentials.
-
Receive role-based permissions.
-
Ensure all administrative actions are auditable and traceable to specific users.
The setup has three main steps:
-
Create a new role (or modify an existing one) to provide permissions to Keycloak-specific actions.
-
Map the role to your identity provider so administrators can authenticate via SSO.
-
Inform your admins of the alternative login URL.
Prerequisites
Before you begin, make sure you have:
-
Access to Keycloak in your ONE instance with the fixed admin credentials.
-
An existing SSO identity provider configured in Keycloak. SSO must already be configured for end-user authentication. See Keycloak Active Directory Integration for setup instructions.
Keycloak configuration
Set up role and Keycloak permissions
Configure roles and permissions that allow admins to access Keycloak with appropriate levels of access.
To configure Keycloak administration roles:
-
Navigate to your Keycloak Admin Console.
-
Log in using fixed admin credentials.
-
Select the Ataccama ONE realm (for example,
ataccamaone).
-
Create or select an administration role:
-
Navigate to Realm Roles.
-
Select a role to be used for Keycloak administration. Depending on your organizational and security needs, either use a pre-existing role (for example,
admin) or create a new one (for example,keycloak-admin).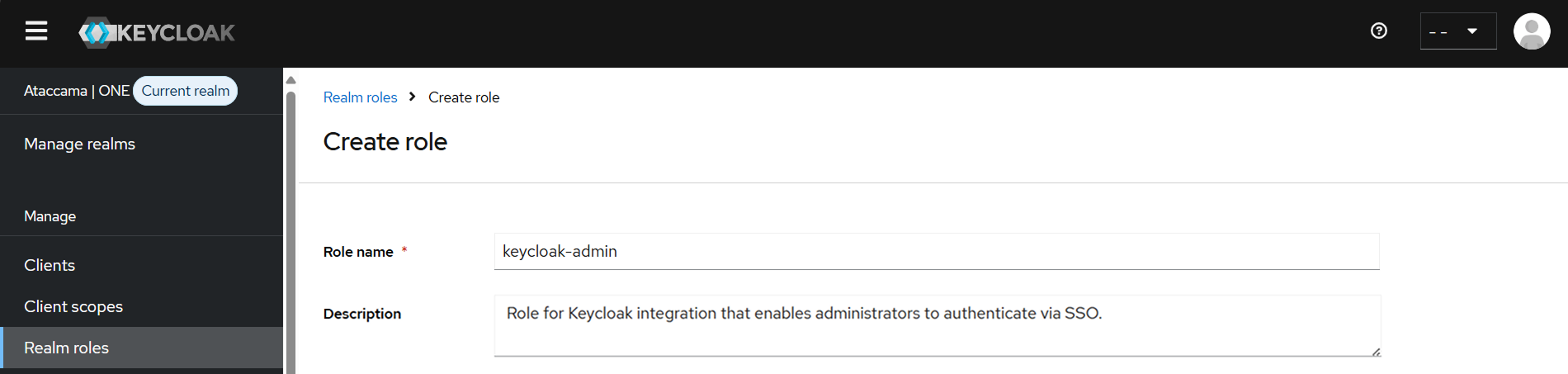
-
-
Assign Keycloak permissions to the role:
-
Open the role and navigate to the Associated Roles tab.
-
Select Assign Role.
-
Filter by clients and select appropriate Keycloak roles based on the actions your admins should perform.
-
At a minimum, this should include:
-
manage-account -
view-applications -
view-profile -
view-realm
-
-
For full platform administration (recommended), assign all permissions related to realms, identity providers, groups, clients, users, and events.
The optional
impersonationrole allows admins to take over a different user’s session. While this action is auditable via the Keycloak Events log, consider whether it is necessary to grant this permission based on your organization’s security policies.
-
-
Select Assign to confirm.
-
Map the role to your identity provider
Map the administration role to your identity provider so that administrators can authenticate via SSO using their individual accounts.
For detailed instructions on mapping roles to your identity provider, see the Map AD groups to Keycloak roles.
Log in via SSO
Once SSO access is configured, administrators using SSO authentication cannot use the standard Keycloak login URL.
To log in to Keycloak via SSO:
-
Navigate to:
<ataccama_instance_url>/auth/admin/ataccamaone/console/#/
This URL directs you to the standard Ataccama login page and allows you to use SSO authentication with your individual credentials.
Was this page useful?
