Audit
|
Exporting audit logs to ONE Object Storage is not available in Ataccama Cloud deployments. |
The Audit tab lets you visualize the information collected by the Audit module. The Audit module is an optional component that retrieves audit logs from Metadata Management Module (MMM), Data Processing Module (DPM), and ONE Data (Data Management Module, or DMM).
Audit logs are stored in an internal audit database. You can change the default retention and cleanup settings for the audit database.
You can also set up a schedule for exporting, retention, and cleanup of audit logs in a designated ONE Object Storage (MinIO) bucket. This option is however not supported in Ataccama Cloud deployments.
For more information about how to configure the Audit module, see Audit Configuration.
|
Take note of the following: |
Overview
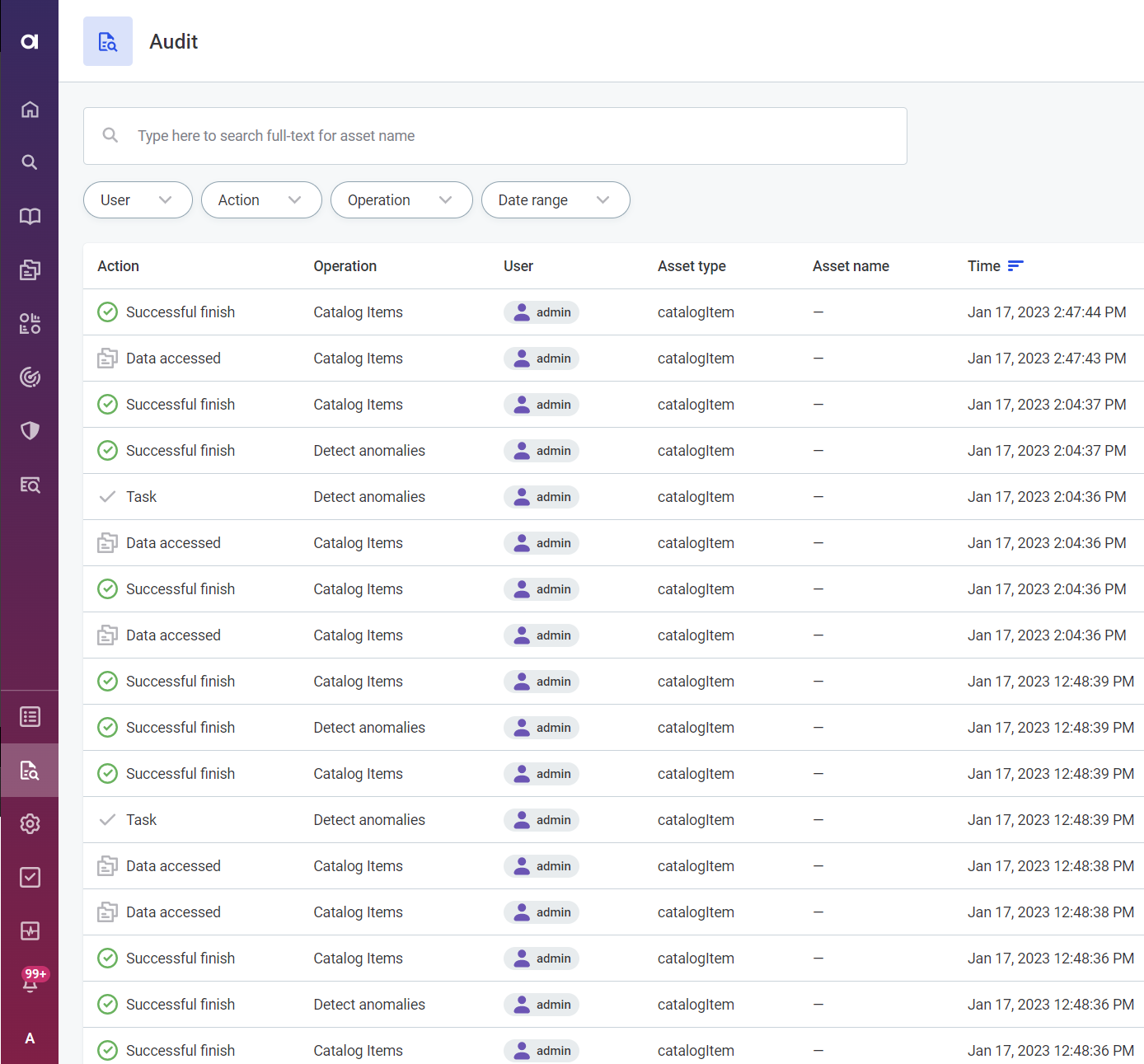
The Audit UI provides a list of all available audit logs with the following information shown for each entry:
-
Action: The type of action performed, for example:
OPERATION,FINISH_SUCCESS,READ. -
Operation: Describes the action taken by user, for example, Access detail, Detect anomalies, List, Check catalog item DQ availability. The values are provided dynamically based on the input from the audited modules.
-
User: The name of the user responsible for the action.
-
Asset type: The type of asset, such as
attribute,catalogItem,connection,credential,location,source. -
Asset name: The name of the asset. Not available if the asset is not listed.
-
Time: The date and time at which an operation occurred.
You can search the list by asset name or filter based on the user, action, operation, or date range.
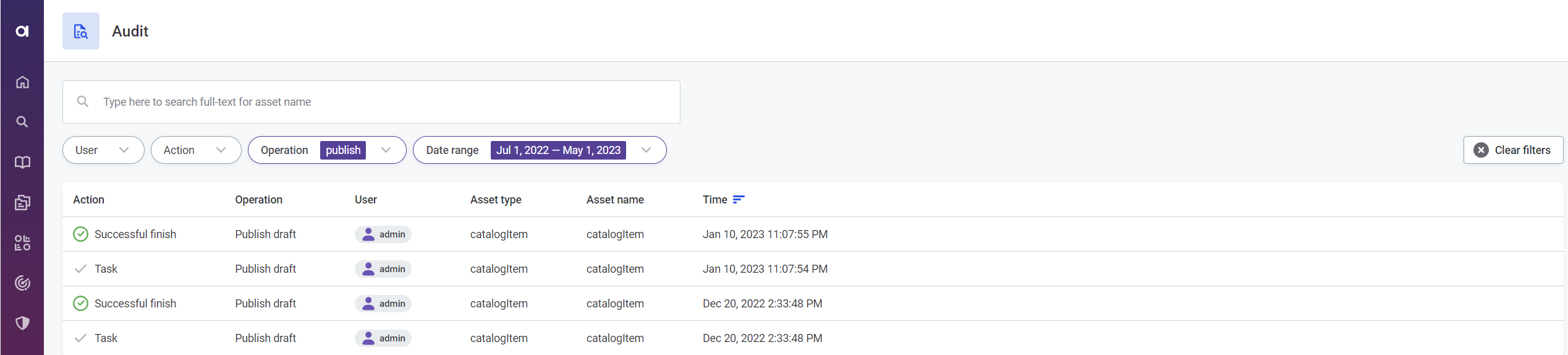
Audit roles and access levels
By default, only the admin identity provider role has access to the Audit module.
Before you give access to the Audit module to other users, consider that audit logs contain information about activity and operations related to all data stored in ONE.
The following table lists identity provider roles (Keycloak) and their access levels as related to audit.
| Role | Level of access to audit |
|---|---|
|
Full access to audit logs and retention settings. |
|
Full access to audit logs and retention settings. |
|
Full access to audit logs. |
View entry details
To display more details about a particular audit log entry, select the entry from the list. The information is grouped as follows:
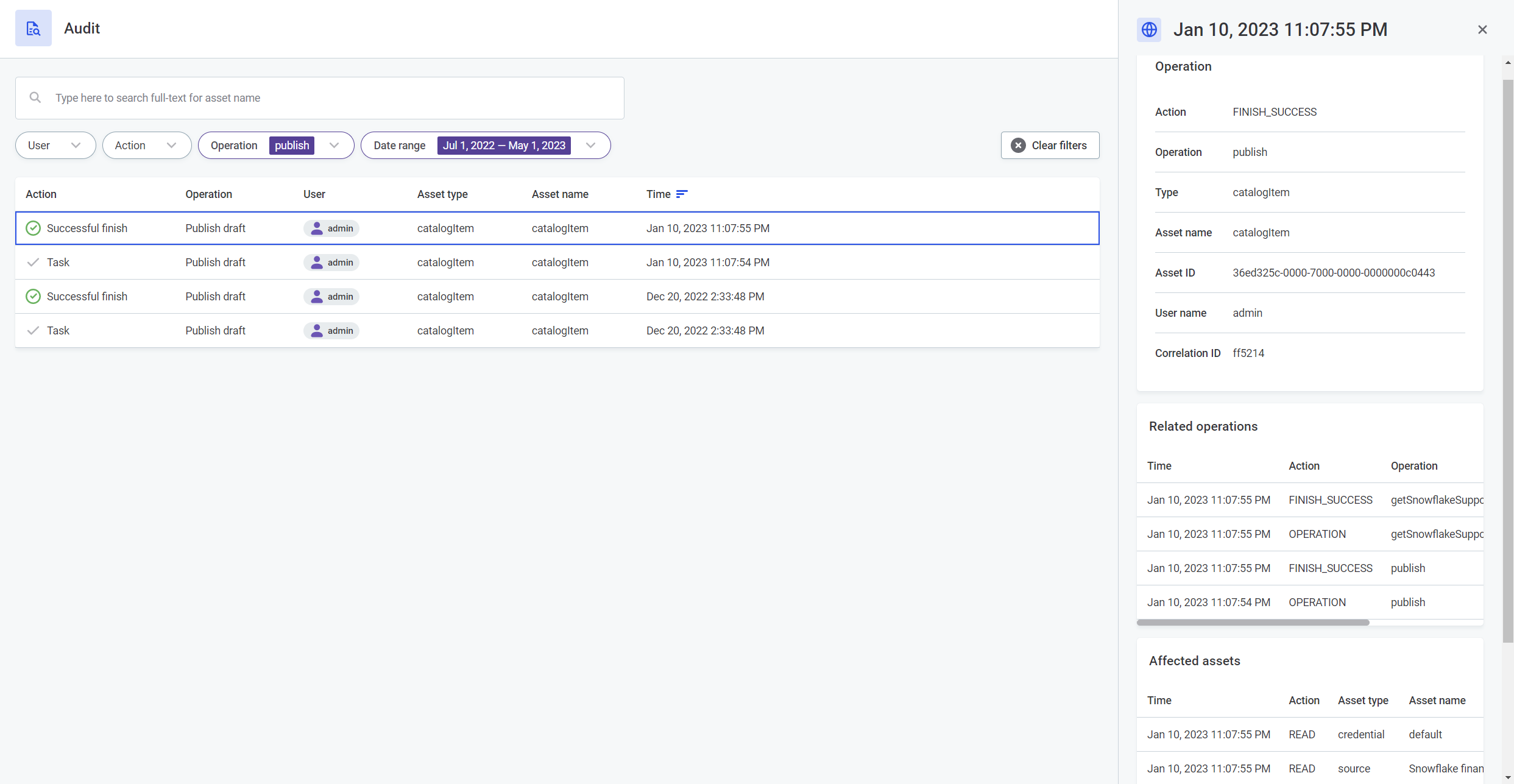
-
Operation: In addition to Action, Operation, Type (Asset type), Asset name, and User name (User), which are already shown in the audit logs overview, the detailed view provides the following:
-
Asset ID: The unique identifier of the asset. Not available if the asset is not listed.
-
Correlation ID: The identifier that links the asset to all the operations related to that asset. See Related operations.
-
-
Related operations: A list of operations associated with the selected operation or asset. For each operation listed, you can see the following information: Time, Action, Operation, Asset type, Asset name.
-
Affected assets: A list of assets that were accessed in order to fulfill the action taken by user. For each asset, the following information is shown: Time, Action, Asset type, Asset name.
-
(Optional) Additional information: Some operations contain a list with additional information. With some properties, you can drill down for more details. The included information depends on the type of operation.
|
For example, operations related to user access management configuration (Manage access and Transfer stewardship) include details about the access levels and any groups and users involved in the transfer or assignment of access and stewardship. 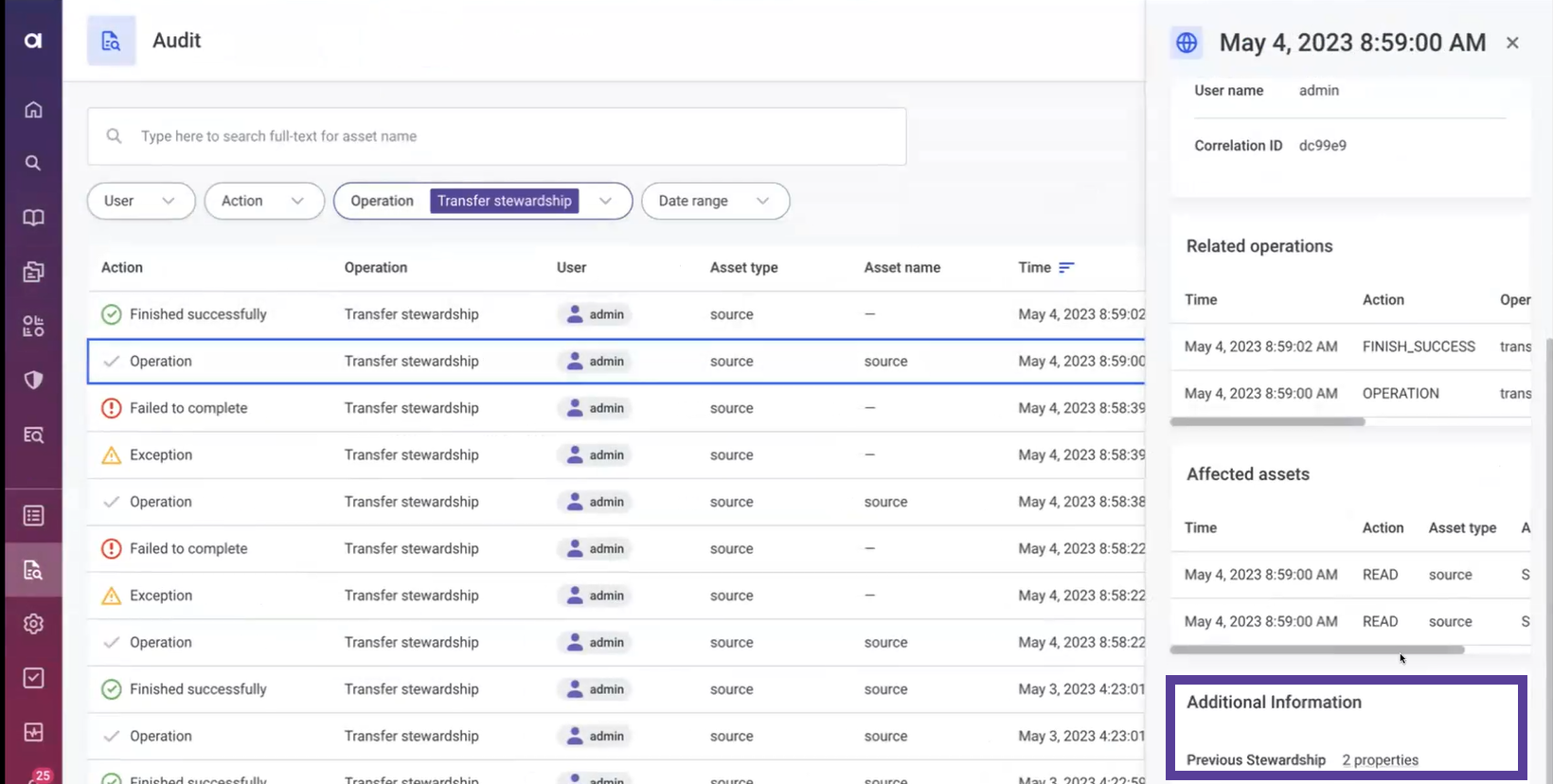
|
Change audit retention settings
By default, audit logs are stored in an internal audit database for 90 days in newly installed environments and upgraded environments without preexisting audit logs. In environments with preexisting audit logs, the default retention is extended to one year.
The age of an audit log is always counted from the date it was created. The date it was exported to ONE Object Storage is not considered.
You can change retention settings directly from the Audit module. However, the following properties are only available if you have enabled and configured exporting to a designated ONE Object Storage (MinIO) bucket:
-
Export to ONE Object Storage after
-
Delete from ONE Object Storage after
|
The default maximum allowed retention period is one year.
If you need to retain audit logs that are older than one year, you can change the relevant retention properties in To avoid loss of audit logs that are older than one year, make these changes before you start the Audit service during the upgrade procedure. For more information, see ONE Gen2 Upgrade Guide, Audit Module Upgrade section. |
Take note of the following:
-
If export or cleaning frequency is set to one day, the Audit module exports or cleans data from the previous day (by date, with midnight being the cutoff point).
-
To prevent removal of logs from the audit database before they are exported, the value of Remove from the audit database after property must be higher than the value of Export to ONE Object Storage after property.
To change audit retention settings:
-
Go to Audit.
-
From the three dots menu, select Audit retention settings.
-
Choose a frequency of export and cleanup for the following properties:
-
Export to ONE Object Storage after: (Optional) Available only if the Export feature is configured.
-
Remove from the audit database after
-
Delete from ONE Object Storage after: (Optional) Available only if the Export feature is configured.
-
Export audit logs to ONE Object Storage
| In this version, the feature is experimental. |
When the Export feature is configured, audit logs can be exported from the audit database to a designated ONE Object Storage (MinIO) bucket following a predefined schedule. It is also possible to define how often the exported files are cleaned.
Audit entries are exported in the form of two CSV files, one for operations (audit_export_operations_YYYY-MM-DD.csv) and one for accessed assets (audit_export_assets_YYYY-MM-DD.csv).
Files follow the same structure that is used in the audit database, with the exception of the module name that is not stored in a separate table in this case. The following schemas are used:
-
Operations:
"id","correlationId","user","userId","userName","time","action","operation","assetType","assetName","assetId","moduleName","violation","details". -
Assets:
"id","correlationId","type","assetType","assetId","action","violation","moduleId","moduleName","moduleHost","time","user","assetName","userId","userName".
To enable exporting, the following requirements must be met:
-
In the Audit module configuration, set up the connection to ONE Object Storage using the following properties:
ataccama.one.object-storage.storages[0].is-default=true ataccama.one.object-storage.storages[0].storage-id=export ataccama.one.object-storage.storages[0].env=test; ataccama.one.object-storage.storages[0].storage-type=MINIO ataccama.one.object-storage.storages[0].connectionProperties.url=http://localhost:8091 ataccama.one.object-storage.storages[0].connectionProperties.access-key=minio ataccama.one.object-storage.storages[0].connectionProperties.secret-key=minio-secret ataccama.one.object-storage.storages[0].connectionProperties.tmp-expiration=3600000For more information, see ONE Object Storage Configuration and Audit Configuration. -
In the Audit Module configuration, specify how exporting should work.
-
Enable the Export feature through the following property:
ataccama.audit.export.enabled=true -
Provide additional information regarding the connection to ONE Object Storage, such as the storage identifier and the bucket name. If you are not using the default value for
ataccama.audit.export.storage-id, make sure to update the propertyataccama.one.object-storage.storages[0].storage-idaccordingly.ataccama.audit.export.storage-id=export ataccama.audit.export.bucket-name=audit-export -
(Optional) Edit the following properties if you do not want to use the default values for exporting and cleaning schedules.
The exporting and cleaning schedules use Cron expressions. By default, the Audit module attempts to export data from the previous day every two hours if the logs are not already exported.
ataccama.audit.export.cron=0 0 1/2 ? * * ataccama.audit.export.cleanup-cron=0 0 1 * * ? -
(Optional) Change the maximum audit log retention and export settings using the following properties. The default value for all three properties is one year. Only change the value if you need to retain audit logs for a longer time period.
The value is set as an integer expressing the number of days of retention. However, this number is then rounded to the nearest number of days based on the following scale.
Expand to see the audit logs retention scale
-
1 day (number of days: 1)
-
1 week (number of days: 7)
-
2 weeks: (number of days: 14)
-
1 month: (number of days: 30)
-
2 months: (number of days: 60)
-
3 months (number of days: 90)
-
6 months (number of days: 180)
-
9 months (number of days: 270)
-
1 year (number of days: 365)
-
2 years (number of days: 730)
-
5 years (number of days: 1825)
-
10 years (number of days: 3650)
-
20 years (number of days: 7300)
# Maximum number of days audit logs can be retained in the audit database before they are deleted. Default value: 365. ataccama.audit.export.max-db-retention # Maximum number of days audit logs can be retained in the audit database before they are exported to a designated ONE Object Storage (MinIO) bucket. Default value: 365. ataccama.audit.export.max-export-threshold # Maximum number of days audit logs can be retained in a designated ONE Object Storage (MinIO) bucket. Default value: 365. ataccama.audit.export.max-export-retention -
-
-
To be able to retrieve the exported audit logs using the MinIO/S3 API, make sure you have the necessary credentials for ONE Object Storage.
Was this page useful?
