Okta Integration
Security Assertion Markup Language (SAML) is a protocol for authenticating user access to web applications. Often, user identities are stored across discrete applications and organizations – SAML allows these federated apps and organizations to communicate and trust one another’s users. SAML provides a way to authenticate users to third-party web apps by redirecting the user’s browser to a company login page, then after successful authentication on that login page, redirecting the user’s browser back to that third-party web app where they are granted access.
In the following page, we will cover SAML configuration for Ataccama products using Okta.
For versions 12.5.0 onwards, you need to add saml-post-form.ftl file into <ataccama.home>/keycloak/themes/ataccamaone/login folder before you start the Okta and Keycloak configuration.
You can download the file from here: saml-post-form.ftl.
|
Prepare Keycloak realm for integration with Okta
| If you are using a single Keycloak instance for multiple Ataccama products (ONE, RDM, MDC, etc.) and want to set up individual Okta connections on each of the products, you need to split the existing Ataccamaone realm to several realms (one realm per product). To do this see [Split Atacammaone Realm]. You can then follow the instructions below. |
Before starting the OKTA configuration, we need to gather some information from Keycloak. Follow the next steps:
-
Login to the Keycloak Administration Console.
-
Open Ataccamaone realm in Keycloak.
-
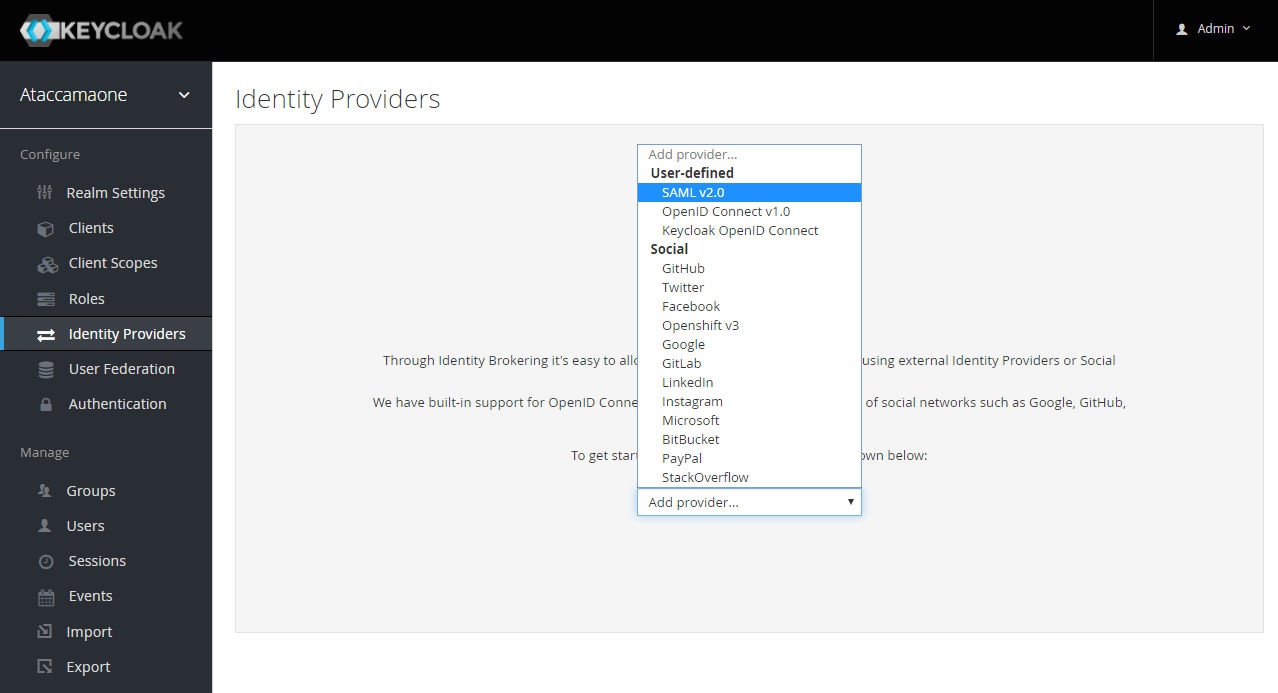
Go to the Identity Providers.
-
From the dropdown list select SAML v2.0.
-
The Add identity provider screen will open, setup the Alias 'LoginWithOkta' – this alias will be used in the redirect URL. You can also add a Display Name which will be visible on the Ataccama Login page.
-
Add any value into the Single Sign-On Service URL field temporarily, in order to be able to save the Identity Provider details.
-
Select Save.
-
Keep Add identity provider window open, we will come back to it later when we will have Okta configuration ready.
Split Ataccamaone realm
If you are using a single Keycloak instance for multiple Ataccama products (ONE, RDM, MDC, etc.) and want to set up individual Okta connections on each of the products, we need to split the existing Ataccamaone realm to several realms (one realm per product).
In this example we will create a new Realm for RDM:
-
Go to Keycloak folder at the Ataccama build.
-
Copy
ataccamaone.jsonfile and name itataccamardm.json. -
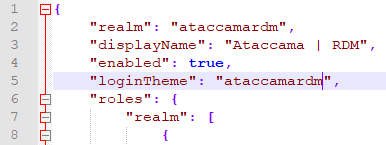
Open newly created
ataccamardm.jsonfile and changeataccamaonetoataccamardmfor both occurrences at the top of the file:CLick here to expand…
-
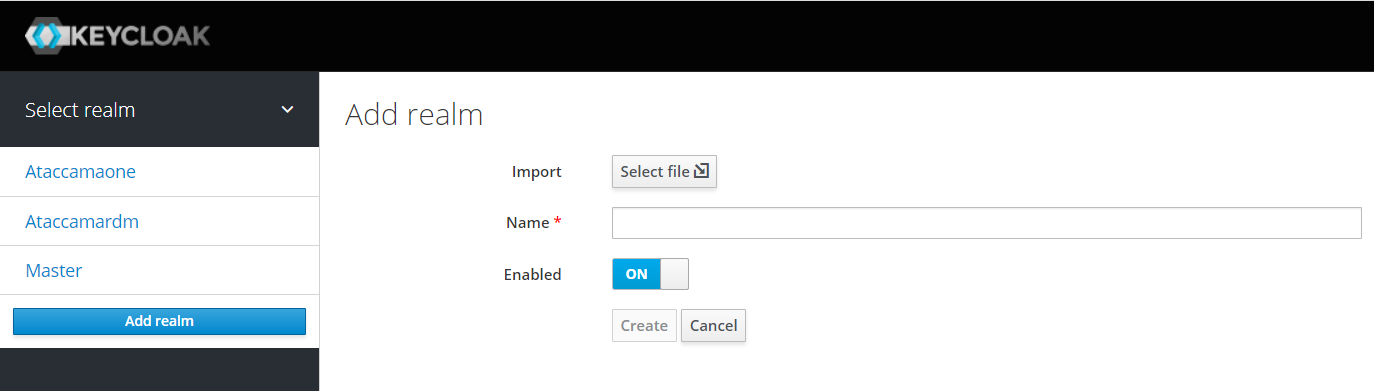
In the Add realm page in the Keycloak, import the
ataccamardm.jsonfile:CLick here to expand…
-
Configure the relevant clients:
-
one-rdm-steps. -
one-rdm-webapp.
-
-
Go to the server and update the following RDM application files by pointing them to the new
ataccamardmrealm (i.e. changeataccamaonetoataccamardmwherever it occurs):-
tomcat/webapps/dqit/WEB-INF/keycloak-steps.json. -
tomcat/webapps/dqit/WEB-INF/keycloak-webapp.json.
-
-
Now you can access RDM through the newly created realm, you can configure Okta for this realm following the guide as normal.
Set up a custom SAML application in Okta
To integrate Okta with Keycloak, follow the steps below:
-
Login to your Okta portal.
-
Select Admin.

-
From the OKTA Dashboard, click Add Applications.
-
Select Create New App.
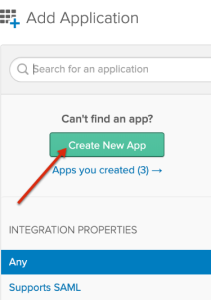
-
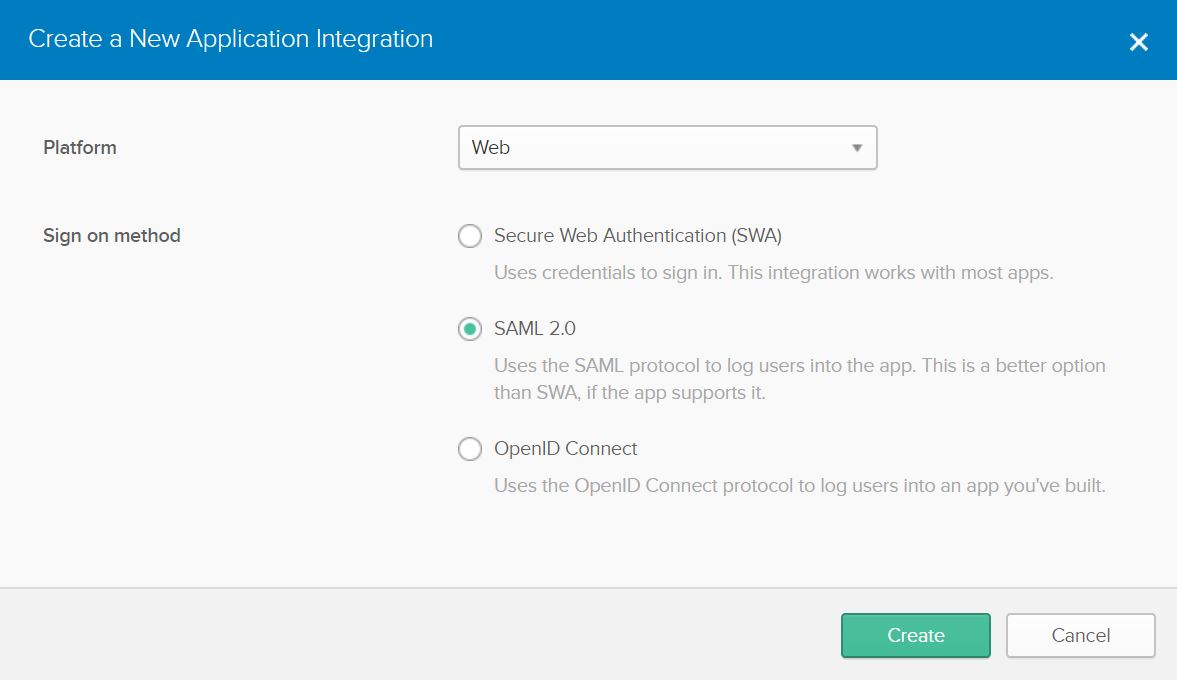
The Create a New Application Integration dialog box will appear. Ensure Web is selected under Platform, select SAML 2.0 under Sign on method, and click Create.
-
In General Settings define the App name as
Ataccama. This is the name that will be visible in your Okta applications. You can also add the logo (optional).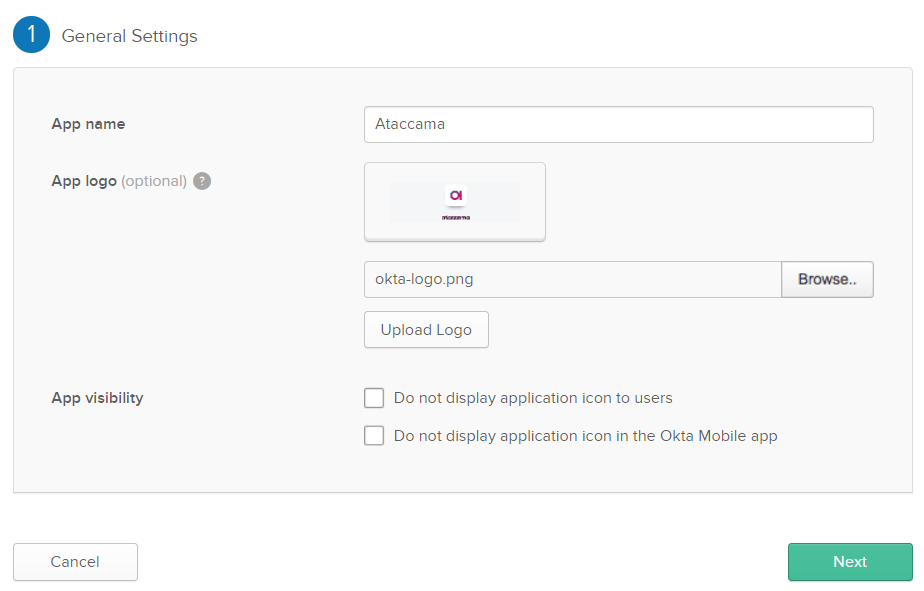
-
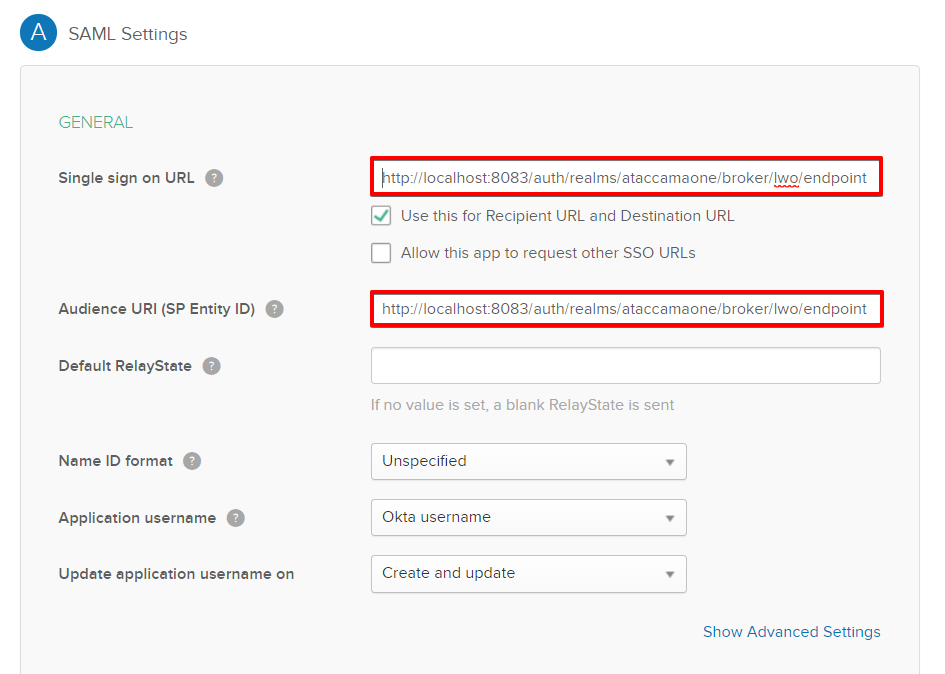
In SAML Settings, copy Keycloak’s Redirect URL to Single sign-on URL and Audience URI (SP Entity ID).
-
Add Attribute Statements: firstName, lastName, and email. The same name will be used further in the Keycloak Identity Provider Mapper.
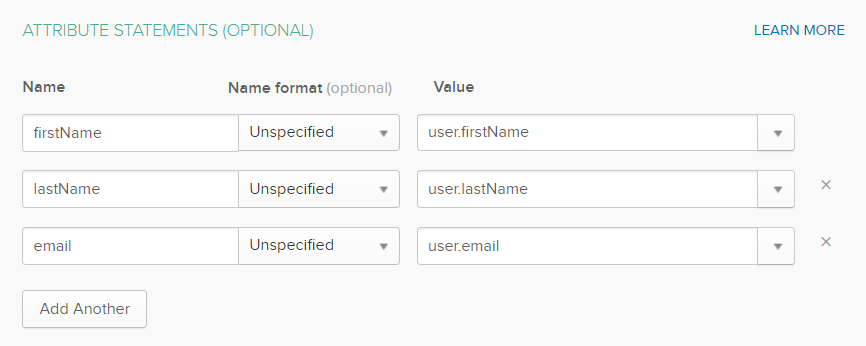
-
Configure the application type (select I’m an Okta customer adding an internal app and This is an internal app that we have created), and then click Finish.
-
Assign people to the newly created Okta application.
-
Now the application has been added to Okta, you need to copy the Identity Provider metadata link and import it into Keycloak in the Add identity provider window which should still be open. To do this click on the Identity Provider metadata link in Settings to open the xml file in a new tab – copy the link.
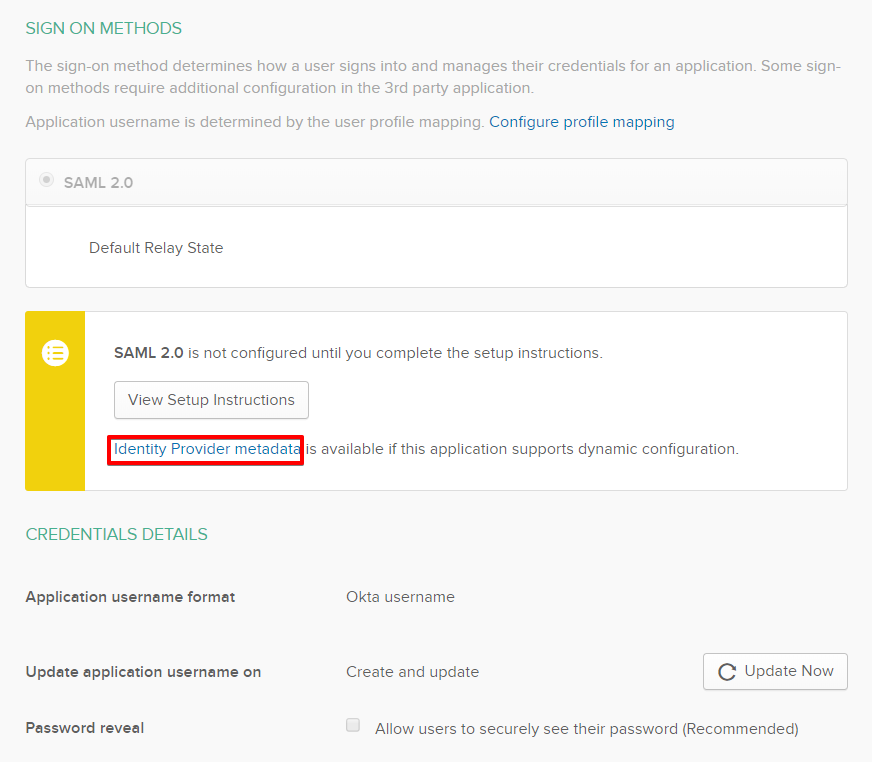
Keycloak realm integration (continued)
Return to the open Add Identity Provider page, and follow the steps below:
-
Scroll to the bottom of the page until you find the Import External IDP Config section and paste the metadata link into the Import from URL field.
-
Select Import.
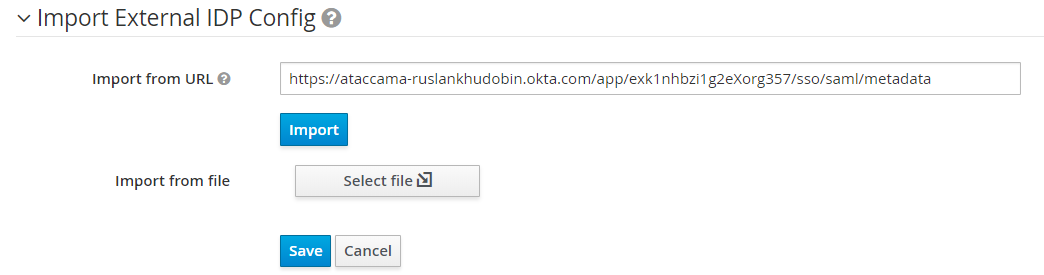
-
The SAML Config section should now be updated according to the imported metadata.
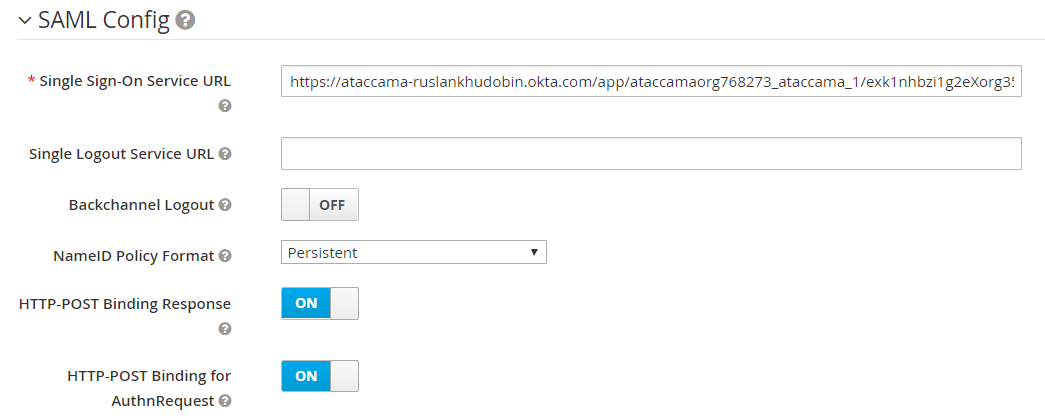
-
Check the First Login Flow is set as
first broker login.
-
Open the Mappers tab, and then select Create.
-
Fill the Add Identity Provider Mapper form according to the Attribute Statements added in Okta. You will need to repeat it 3 times for each Attribute Statement:
firstName,lastName,email. The Name field can be custom for Keycloak, but all other fields should match what is defined in Okta.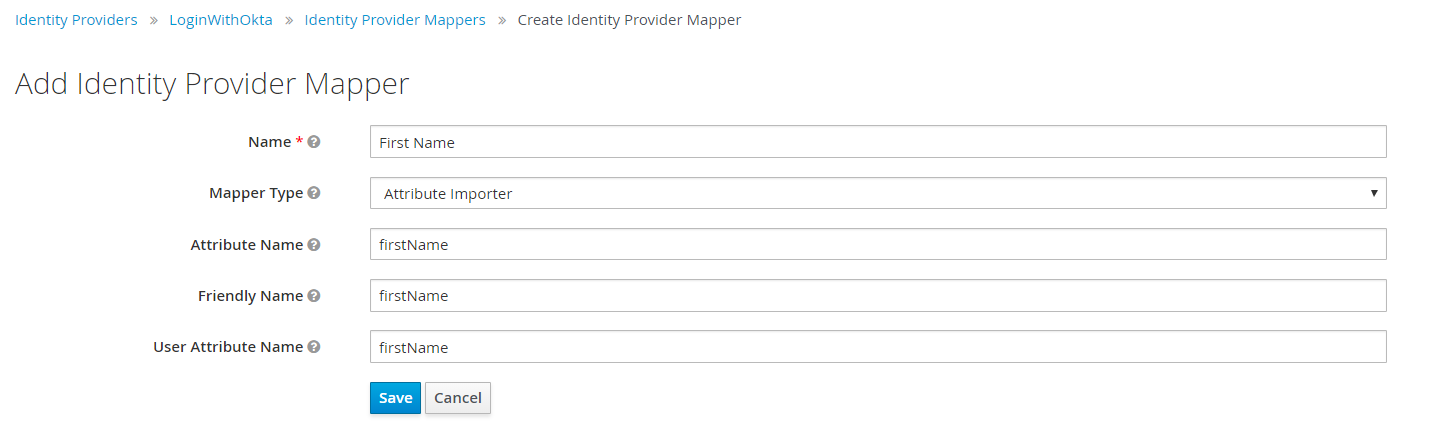
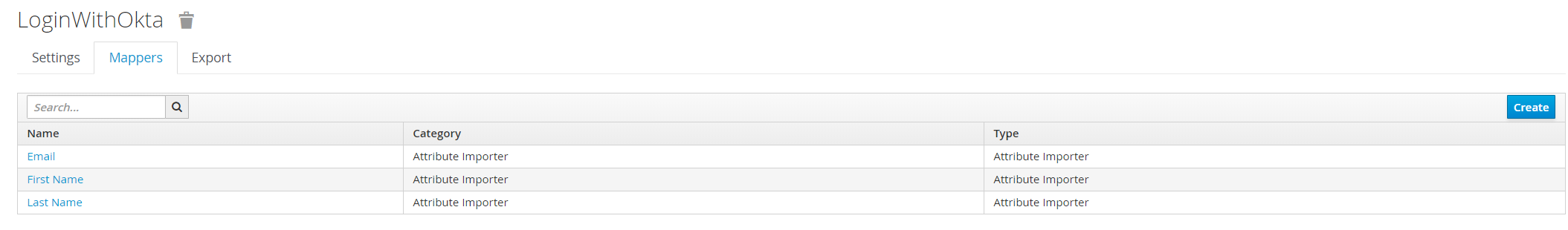
-
Once all 3 Attribute Mappers are added it should look like this.
Set permissions in Okta-Keycloak through the active directories
You can manage roles via Okta and assign a role in Keycloak based on the Okta attribute. To do this, use the steps below:
-
Add an additional Attribute Statement to Okta. As an attribute value, you can pass a logic which will assign value based on the Active Directory name of the group.
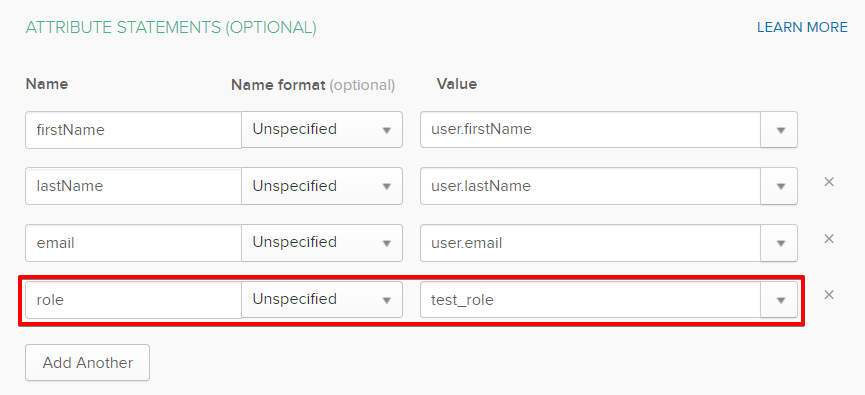
-
Add the additional mapper into the Identity Provider Mappers window in Keycloak.
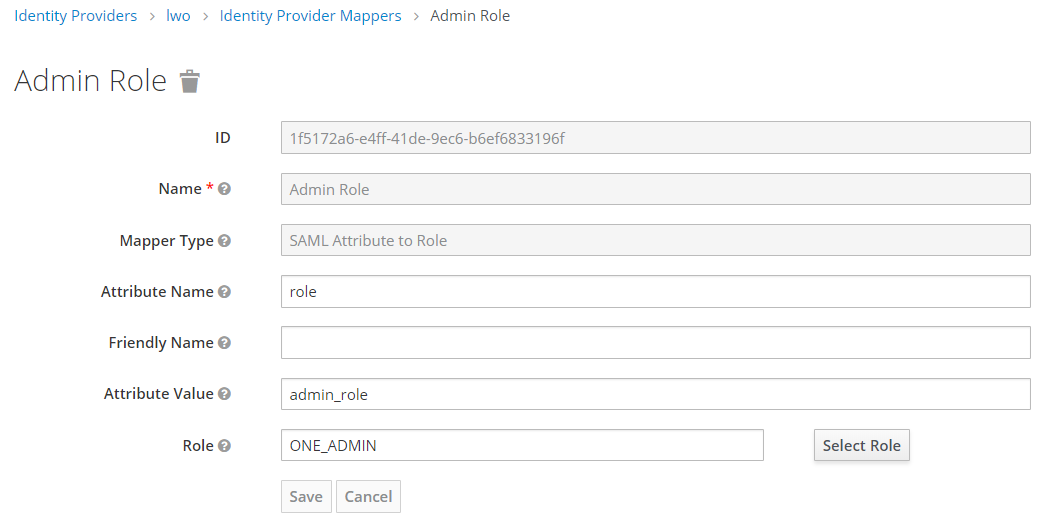
You can create multiple SAML Attribute to Role mappers for each Active Directory Group and assign multiple roles (a new mapper is required for each role added).
Ensure to leave Friendly Name blank, otherwise the Mapper will fail as it will not be able to locate this attribute and value in Okta.
Once all these steps have been completed, each time a user will log in into Ataccama ONE, user permissions will be verified according to a user’s Active Directory group and assigned to its roles. When you open the Ataccama ONE login page you will see the option to Login With Okta.
Was this page useful?
