Unique Encryption Keys
Generate individual encryption keys to secure the connection between ONE Desktop and your Ataccama Cloud deployment. This guide provides instructions about how to generate unique encryption keys in Cloud Portal and supply them to ONE Desktop, local runtime, and hybrid Data Processing Engine (DPE).
Overview
Using unique encryption keys contributes to overall security in the following ways:
-
It provides additional protection against unauthorized access to your data and environment in Ataccama Cloud.
-
It makes sure data is encrypted and compliant with data protection regulations.
-
It helps mitigate data leakage risks and protects data in transit and at the edge of the network.
-
It secures communication between ONE and edge components, such as hybrid DPEs and ONE Desktop.
Unique encryption keys can also be easily rotated as well as securely backed up and restored without getting embedded in the backup.
The keys are provided as JCE keystore files, encoded as Base64 strings.
Create keystore
To generate your keystore:
-
In Cloud Portal, go to your environment and switch to the Services tab.
-
In Shared Services, find ONE Desktop and select Instructions.
-
In Use keystore file, select Generate to create the keystore.
-
Once the keystore is ready, download the keystore file (Download keystore.jceks) and copy the corresponding password.
Keep the modal open until you are finished with the configuration in case you need to return to it again. Otherwise, you have to generate a new keystore and password. 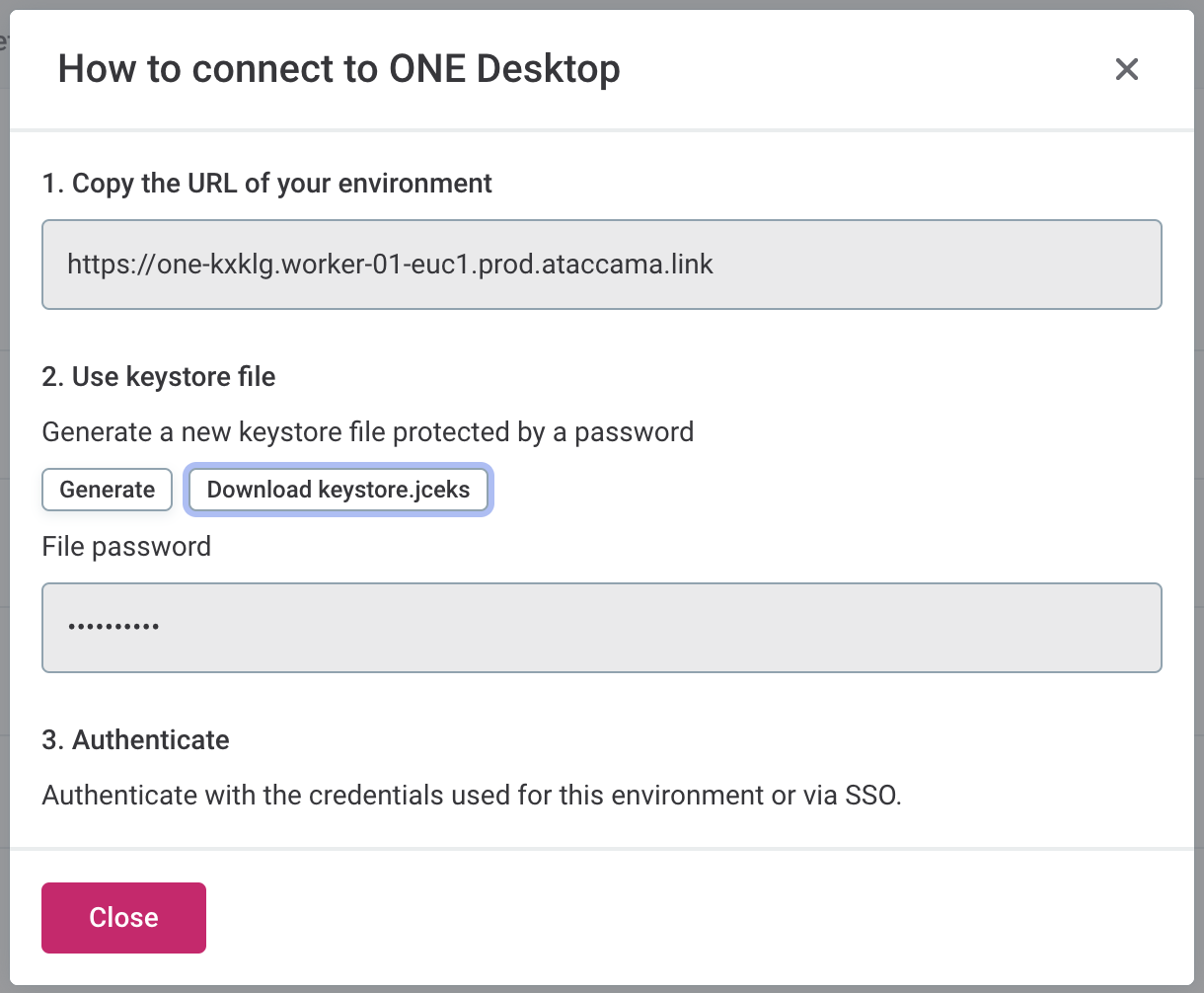
Configure ONE Desktop to use the keystore
-
Navigate to your ONE Desktop installation folder.
-
Open the
one-desktop.inifile in a text editor. -
Add the following properties. Make sure to provide the correct path to the downloaded keystore as well as the keystore password (see Create keystore, steps 3 and 4):
-Dproperties.encryption.keystore=[PATH_TO_DOWNLOADED_KEYSTORE_FILE] -Dproperties.encryption.keystore.password=[KEYSTORE_FILE_PASSWORD] -Dproperties.encryption.keyAlias=initial_peripheral -Dinternal.encryption.keystore=[PATH_TO_DOWNLOADED_KEYSTORE_FILE] -Dinternal.encryption.keystore.password=[KEYSTORE_FILE_PASSWORD] -Dinternal.encryption.keyAlias=initial_peripheral -
Save your changes.
-
To apply the properties to the local runtime, launch ONE Desktop.
-
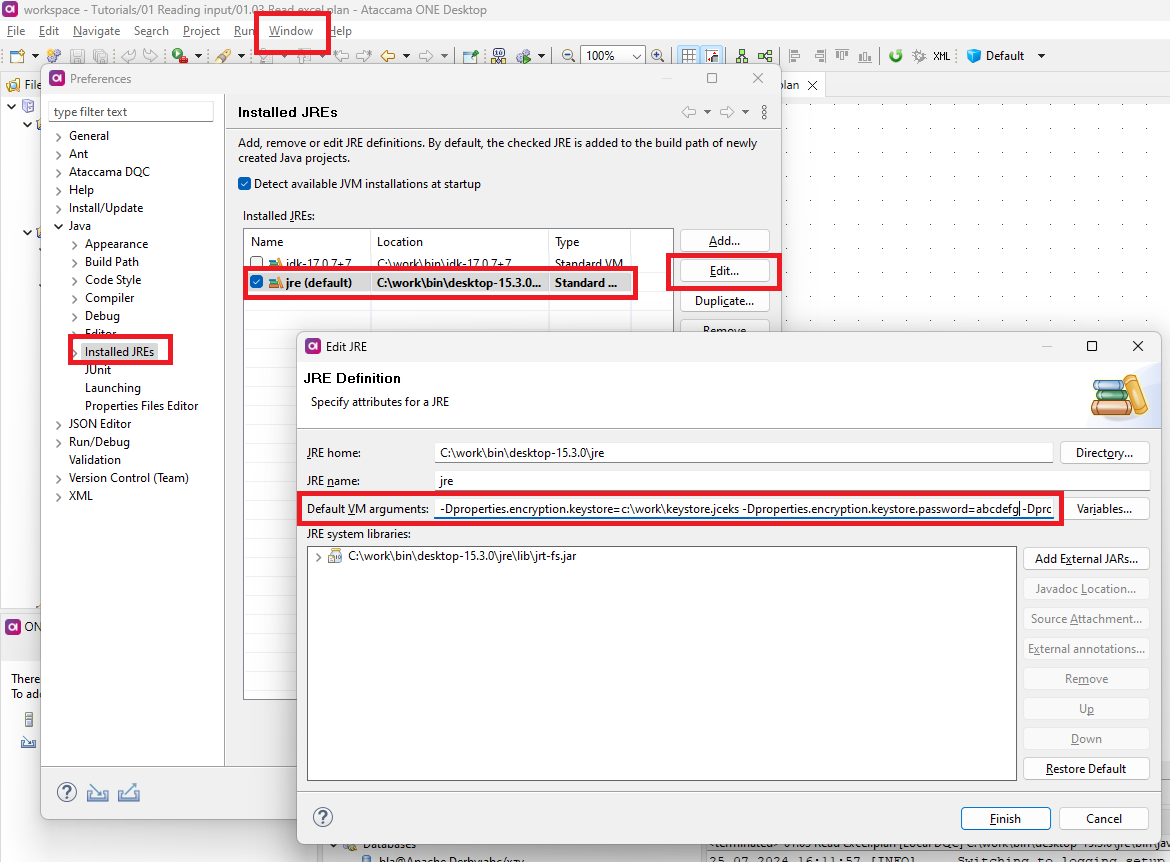
Go to Window > Preferences > Java > Installed JREs.
-
Select the default JRE and then Edit.
-
In Default VM arguments, paste the properties listed in step 3.
-
Select Finish and then Apply and Close to save the changes.
Configure self-managed DPE to use the keystore
Self-managed hybrid DPEs connecting to Ataccama Cloud must use the same keystore.
For details, see Kubernetes-Based Hybrid DPE Deployment Guide.
Update encryption keys after credentials rotation
When credentials are rotated, you might need to update the encryption keys used for securing connections. This ensures the integrity and security of your environment.
To do so:
-
Use the Java
keytoolutility to generate a new keystore:keytool -genkeypair -alias myKeyAlias -keystore myKeystore.jks -storepass myStorePass -
Store the keystore securely. You will need it for later configuration.
-
Modify the
JAVA_OPTSenvironment variable to include the following properties:-Dproperties.encryption.keystore=/path/to/myKeystore.jks -Dproperties.encryption.keystorePassword=myStorePass -Dproperties.encryption.keyAlias=myKeyAlias -
Restart all affected components to apply the updated encryption key configuration.
Was this page useful?
