Architecture
Ataccama Edge architecture is built on two core principles:
- Bring your own storage
-
All sensitive data remains in customer-provided object storage. The current version supports AWS S3 buckets.
- Bring your own cloud
-
Your organization provides a cloud account with configured networking and permissions. Ataccama deploys and maintains processing components through automation while you retain full ownership of the environment.
Architecture overview
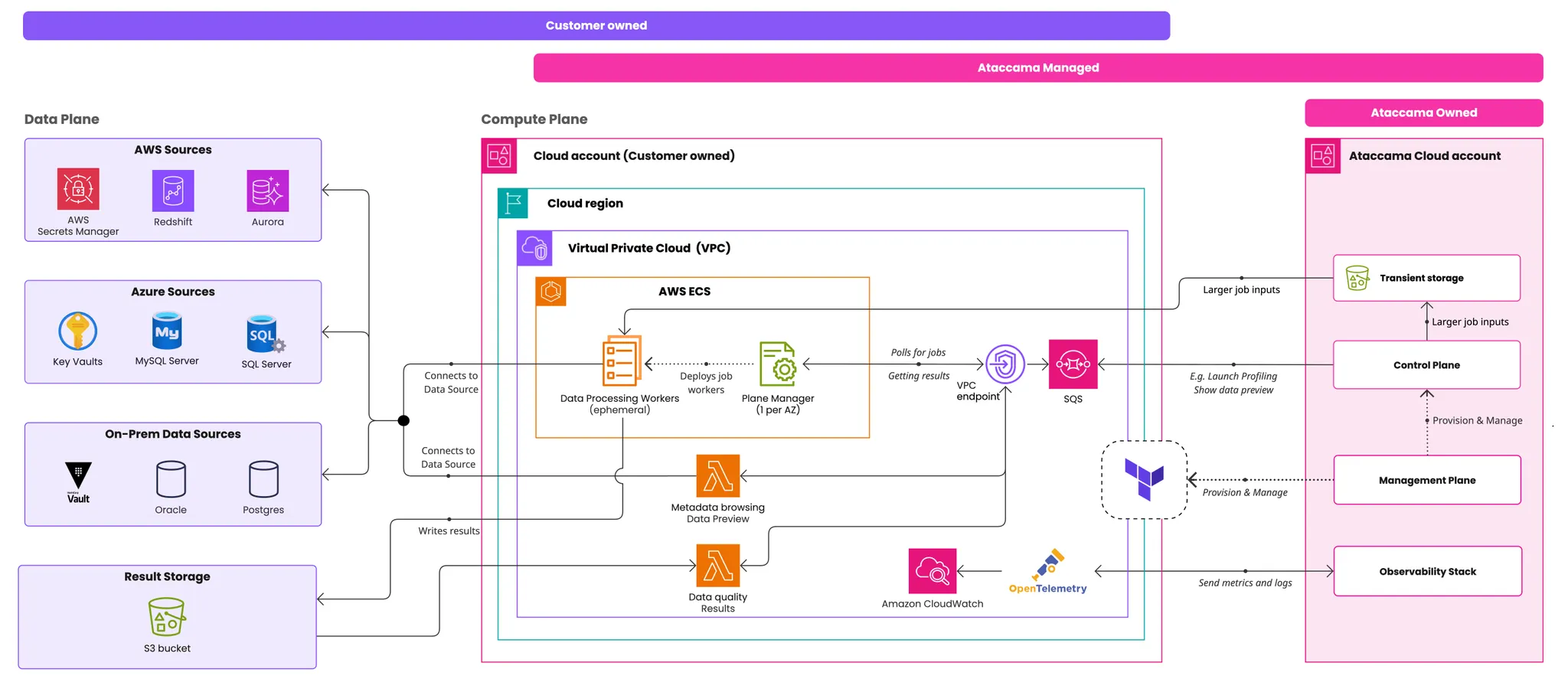
The architecture separates processing and data management across four distinct planes:
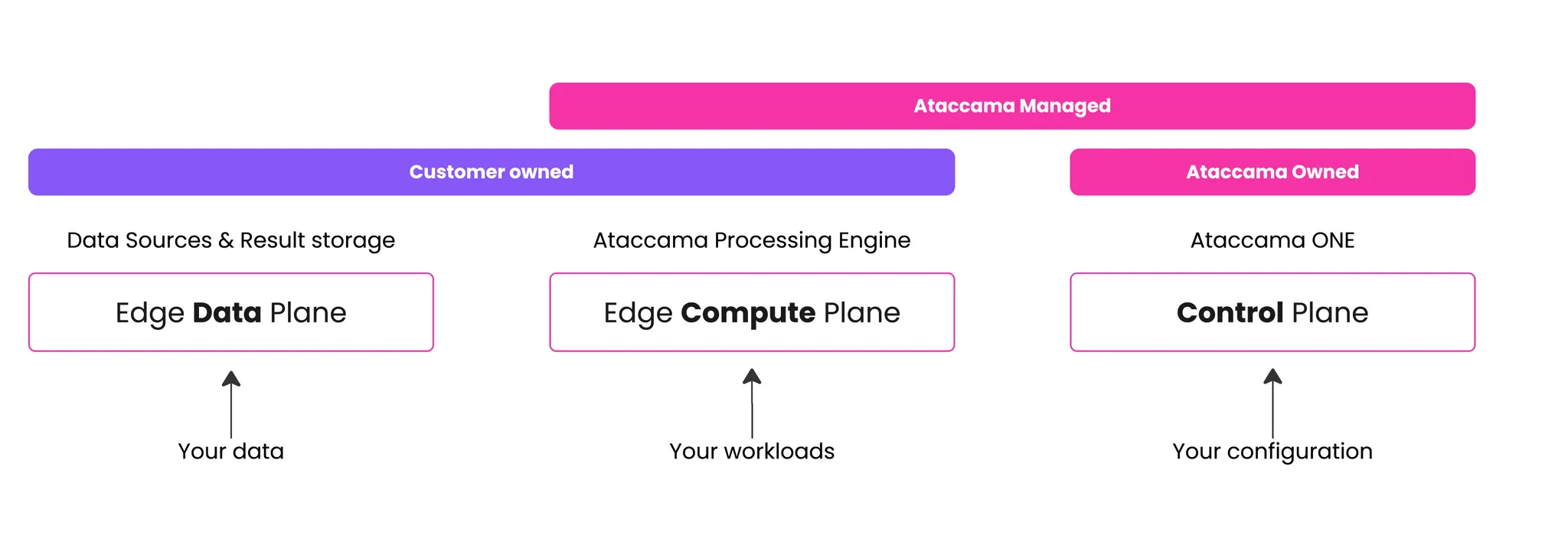
Edge compute plane
Location: Your AWS account.
Description: Runs components that process data from the data plane (primary data) but doesn’t directly store any data.
Management: Ataccama-managed software on customer-owned infrastructure.
Data plane
Location: Your environment.
Description: Stores primary data and sensitive processing results from the compute plane. Primary data never leaves this plane except short-term for viewing and processing, and when explicitly imported as reference data.
Management: Customer-owned and managed.
Control plane
Location: Ataccama Cloud accounts.
Description: The place where you browse metadata, set up DQ rules, and view processing results. Cannot directly access your data and does not store it in any way (direct or derived).
Management: Ataccama-owned and managed.
Management plane
Location: Ataccama Cloud accounts.
Description: Provides Cloud Portal as an administrative interface where you provision and upgrade edge instances. Includes automation services that deploy, upgrade, and configure other Ataccama components in both control and compute planes.
Management: Ataccama-owned and managed.
Security and communication
All communication between planes uses TLS 1.3 encryption. Data is encrypted at the application level both in transit and at rest.
All sensitive data is encrypted on application level when stored in the result storage.
Key communication patterns:
-
Management to other planes: No direct access. Uses ArgoCD and Terraform Cloud for configuration management.
-
Control to compute plane: Communicates via message queues and pre-signed URLs for transient storage.
-
Job execution flow:
-
Control plane sends job request via message queue.
-
Compute plane retrieves job image from OCI registry.
-
Job processes data and writes results to your S3 bucket.
-
Metadata returns to control plane.
-
|
The data plane includes all data sources wherever they are stored if they can be connected to the control plane via standard data source or connector mechanisms.
The compute plane can also use provided secrets storage to retrieve credentials. It stores sensitive results in an S3 bucket via the provided IAM role.
Was this page useful?
